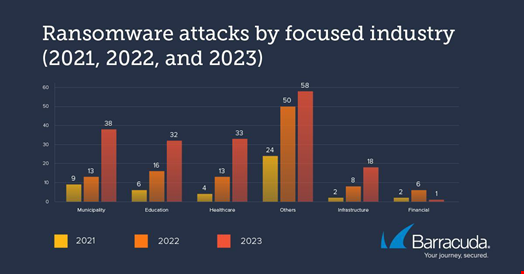
Government agencies alongside education and healthcare organizations have become prime targets for ransomware operators over the past three years.
According to a new report published on August 2, 2023, by data protection provider Barracuda Networks, the number of reported attacks against municipalities, education and healthcare has doubled since last year and more than quadrupled since 2021.
Attacks against infrastructure-related industries have doubled over the same period.
The Barracuda researchers believe that ransomware actors favor municipalities and education “because they are resource-constrained.” Healthcare and infrastructure organizations are lucrative targets because these industries “have an immediate and potentially severe impact on human lives, which cybercriminals try to exploit to increase the likelihood of getting paid.”
“In many countries, one or more of these sectors may be legally obligated to report cybersecurity incidents, which makes the impact more visible as well,” reads the report.
Overall attacks are increasing and Barracuda saw a rise in reported ransomware incidents in almost all of the 21 other sectors the firm analyzed.
Generative AI, a Ransomware Enabler
The analysts argue that the emergence of generative AI tools like large language model-enabled (LLM) chatbots has contributed to the most recent ransomware surge.
On the one hand, using generative AI’s writing capabilities, cyber-attackers “can now strike faster with better accuracy, as the spelling errors and grammar issues in phishing emails are more easily eliminated, making attacks more evasive and convincing.”
On the other, they “can use the code-generation capabilities of generative AI to write malicious code for exploiting software vulnerabilities. With these changes, the skill required to start a ransomware attack could be reduced to constructing a malicious AI prompt and having access to ransomware-as-a-service tools, leading to a whole new wave of attacks.”
Read more: Dark Web Markets Offer New FraudGPT AI Tool
For this study, Barracuda analyzed 175 publicly reported successful ransomware attacks worldwide between August 2022 and July 2023.
“The sample size is small because the overwhelming majority of attacks are stopped before they become incidents. While the volume of publicly reported ransomware attacks has doubled in some industries, you can be sure the volume of unreported attacks has also increased dramatically,” the company wrote.
Resilience and Recovery Recommendations
Barracuda provided mitigation advice that organizations can implement “even with limited resources” to help recover from a ransomware attack. Those include:
- For your backup solutions: segment and isolate backup systems; use a different user store (e.g. separate Active Directory and or Lightweight Directory Access Protocol), preferably with zero social network presence; use stronger multifactor authentication (MFA) mechanisms instead of push notifications where attackers can implement volumetric attempts causing MFA fatigue; move to zero trust-based authentication with passwordless capabilities, such as biometrics on authorized devices for user interface authentication; use encryption and do not use shared storage with any other workload.
- For your backup and recovery process: protect the policies and documentation with encryption and only allow privileged access; keep your policies and disaster recovery process documentation in another form factor, including printed and physically distributed versions.
- Separate your storage from your admin’s typical operational environment and create an air gap if you can do it safely – using cloud and a zero trust architecture, for example.
- For virtual machine hypervisors: use a designated backup appliance solution when the recovery time objective (RTO) is aggressive.
