For the first time in history, cyber malicious actors have used Anthropic’s Claude Code, a generative AI coding assistant, to conduct cyber-attacks.
The attackers are likely Chinese state-sponsored hackers and deployed the campaigns for cyber espionage purposes, said Anthropic in a report published on November 13.
The targeted organizations included large tech companies, financial institutions, chemical manufacturing companies and government agencies.
These victims of the cyber-attacks saw their systems infiltrated with minor human intervention.
Anthropic assessed that the AI assistant, Claude Code, performed up to 80-90% of the tasks, with only four to six critical decision points per hacking campaign made by the hackers themselves.
Sophisticated Features of New Generation AI Agents Exploited
In mid-September 2025, Anthropic detected early signs of a highly sophisticated espionage campaign.
Upon investigating the case, the security researchers realised that the attackers manipulated Claude Code to attempt to infiltrate roughly thirty organizations. The threat actors succeeded in a small number of cases.
Anthropic described the campaign as “the first documented case of a large-scale cyberattack executed without substantial human intervention.”
The attackers used Claude Code’s agentic capabilities to an “unprecedented” degree, in part because some of the features have only recently emerged:
- The capability for GenAI-powered tools to follow complex instructions and understand context in ways that make very sophisticated tasks possible
- Their access to a multitude of software tools and applications and ability to act on behalf of the users (e.g. to search the web, retrieve data, analyze emails)
- Their ability to make automated (or semi-autonomous) decisions when performing tasks and even chain together tasks
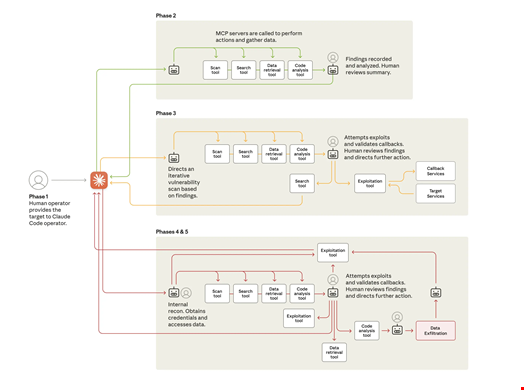
A Six-Phase Attack Flow
Anthropic described a six step attack chain, as follows:
- Campaign initialization and target selection: the human operator chose their target organizations and developed an attack framework, a system built to autonomously compromise a chosen target with little human involvement. This attack framework started with jailbreaking Claude – tricking it to bypass its guardrails – by breaking down the attack into small, seemingly innocent tasks that the AI assistant would execute without being provided the full context of their malicious purpose. They also told Claude that it was an employee of a legitimate cybersecurity firm being used in defensive testing
- Reconnaissance and attack surface mapping: the human operator asked Claude to inspect the target organization’s systems and infrastructure, identify the highest-value databases and report back
- Vulnerability discovery and validation: the human operator tasked Claude with detecting and testing security vulnerabilities in the target organizations’ systems by researching and writing its own exploit code to implant backdoors
- Credential harvesting and lateral movement: the human operator used the AI agent to harvest credentials (usernames and passwords) that allowed it further access
- Data collection and intelligence extraction: the human operator tasked Claude to extract a large amount of private data it had previously identified as valuable information
- Documentation and handoff: the human operator asked Claude to produce comprehensive documentation of the attack, creating files of the stolen credentials and the systems analyzed
After detecting the attacks and mapping the attack lifecycle, Anthropic banned malicious accounts, notified affected entities and contacted competent authorities to provide them with actionable intelligence within ten days.
The GenAI company also expanded its detection capabilities and developed better classifiers to flag malicious activity.
“We’re continually working on new methods of investigating and detecting large-scale, distributed attacks like this one,” the Anthropic report noted.
Despite these measures, Anthropic shared concerns that agentic AI-powered cyber-attacks will continue to grow in volume and sophistication.
“This raises an important question: if AI models can be misused for cyber-attacks at this scale, why continue to develop and release them? The answer is that the very abilities that allow Claude to be used in these attacks also make it crucial for cyber defense,” the Anthropic researchers wrote.
“When sophisticated cyber-attacks inevitably occur, our goal is for Claude […] to assist cybersecurity professionals to detect, disrupt and prepare for future versions of the attack.”
Lack of Actionable Elements for Threat Researchers
The report has widely been shared on social media and within online cybersecurity circles.
While some praised Anthropic for its transparency and others highlighted that this case was the first piece of evidence of a threat they knew was inevitable with the emergence of agentic AI, not everyone is happy with the report.
On LinkedIn, Thomas Roccia, a senior threat researcher at Microsoft, pointed to the lack of actionable information shared in both Anthropic’s public statement and the full report.
He said the report “leaves us with almost nothing practical to use.”
“No actual adversarial prompts, no indicators of compromise (IOCs), no clear signals to detect similar activity. To me it feels a bit like the old days when the antivirus (AV) industry avoided sharing IOCs. Different reasons today (I guess) but the outcome is the same. A high-level story without the material defenders need to take action!”
