Infosecurity News

Saks, Lord & Taylor Payment Card Breach Affects 5 Million
Card-skimming malware was present at stores in North America from May 2017 until March 2018.

Joshua vs. Parker Boxing Match Sees Hundreds of Illegal Streams
Social media was again found to have been a major vehicle for illegal streams, including Facebook, YouTube, Periscope and Twitch.

GoScanSSH Malware Avoids US Military, South Korea Targets
A new strain of malware that targets vulnerable Linux-based systems is loose in the wild.

College Kids Turn to Crypto-Mining, Riddling Higher-Ed Networks
Students are more likely to perform crypto-mining personally as they don’t pay for power, the primary cost of crypto-mining.

Under Armour's MyFitnessPal Sees 150 Million Accounts Compromised
While details of how hackers exploited the accounts are still emerging, this appears to be the largest data breach of 2018 to date.

Infosecurity Magazine System Upgrade: 30th March-1st April
Infosecurity Magazine will be undergoing a system upgrade from Friday 30th March until Sunday 1st April 2018 - more details here

Microsoft Products Are Hackers’ Favorite — Report
Recorded Future claims Flash was less popular in 2017

Boeing Computers Hit by WannaCry
Aerospace giant’s South Carolina facility gets a nasty surprise

FTSE 100 Firms Fail to Share Security Plans
Deloitte finds few even update the board

HiddenMiner Stealthily Drains Androids for Monero Mining
In one case, operators withdrew over $5,000 worth of Monero from one wallet.

Facebook Expands Bug Bounty Amid Spiraling Privacy Scandal
The social network will reward people for reporting misuses of data by app developers.

Legal Departments Struggle with GDPR Role
About half (48%) of legal team respondents in a recent survey claim GDPR is not applicable to their organization.

Cybersecurity Awareness Doesn't Fuel Better Preparation: Report
Businesses still lack the knowhow and resources to defend against data breaches

Twitter Bans Crypto-Currency Ads in Fraud Crack Down
Social giant joins Facebook and Google

UK Mobile Workers Exposed to Public Wi-Fi Risks
VPN use still patchy, says iPass

UK Police Secretly Hoover Up Users’ Smartphone Data
Privacy International calls on Home Office to produce guidance
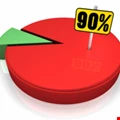
Cloud Security Concerns Surge
90% cybersecurity professionals confirm they are concerned about cloud security, up 11 percentage points from last year.

Bad Bots Make Up a Fifth of All Web Traffic
Gambling companies and airlines suffer from higher proportions of bad bot traffic than other industries.

Energy Sector ICS is the Most-Attacked Infrastructure
40% of industrial control systems in energy organizations were attacked by malware at least once in Q2 2017.

GDPR Spurs 700% Increase in Data Protection Vacancies
Privacy regulation will land in two months’ time



