Infosecurity News

Hacker Halted 2014: Johnny Long Calls for Hackers for Charity Volunteers
The irony was not lost on Johnny Long.

Hacker Halted 2014: Zombies As Scary as a Successful Browser Hack
At the Hacker Halted conference in Atlanta, security researchers Xiaoran Wang and Angelo Prado demonstrated on Thursday some weaknesses in the major browsers in use today.

Sandworm Team Went After Firms Running SCADA
Researchers link C&C servers to attacks on CIMPLICITY HMI software

Calware Back on the Agenda for Resourceful Spammers
Unsolicited calendar invites spike in September as scammers look to bypass filters

Binder Flaw Threatens to Blow Apart Android Security
Check Point researchers say new vulnerability could enable covert data and comms theft

POODLE Gets a Muzzle from OpenSSL
POODLE patch can prevent secure data from being intercepted via a MITM gambit.

Oregon Employment Dept Breach Affects 850K
After being tipped off anonymously, the agency swung into action but is concerned about social security information.

UK in the Crosshairs as EMEA APTs Double
FireEye data suggests targeted attacks are on the rise across EMEA

YouTube Viewers Assaulted by Malicious Ad Ransomware Campaign
Kovter delivered to mainly US online video fans

BlackBerry 10 Vulnerable to MiTM Attack
The flaw affects BlackBerry 10 smartphone customers running the BlackBerry World widget, which device-owners use to search for and download apps.

Seoul Mulls ID Card Overhaul After Series of Catastrophic Breaches
Most identity numbers freely available on black market

Hurricane Panda Hackers Exploit Zero-Day for 5 Months
The advanced Chinese adversary has mounted a heavy cyber-espionage offensive on tech companies.

How to Prepare for a Cybersecurity Career
(ISC)² Foundation and University of Phoenix have developed recommendations to prepare students for cybersecurity careers--and employers for hiring them.

Dropbox: Nope, Not Hacked
The usernames and passwords posted by an anonymous hacker were stolen from unrelated services.

Microsoft Zero Day Traced to Russian ‘Sandworm’ Hackers
Experts urge immediate patching of remote code execution vulnerability
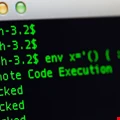
Mayhem Botnet Takes to Shellshock
The Mayhem multi-purpose modular bot for web servers has a new attack vector in the widespread vulnerability.

Android Worm Masquerades as Google App
The Selfmite bug has gotten pushier and more flexible than ever before.

EUROPOL: 100 Cybercriminal Kingpins Control All
EUROPOL said that most of the world’s serious cybercrime is being committed by a "rather limited group of good programmers.”

Snapsaved Admits Photo Hack Exposed Snapchat Users
Third party service loses 500MB of images but says they can't be compiled into searchable database

Facebook Scammers Hide Trojans in Fake Emma Watson Videos
Harry Potter actress used as lure once again to snare over-eager netizens



