Researchers from European cybersecurity vendor ESET have found previously undocumented custom backdoors and tools used by a relatively new APT group called Polonium.
First discovered in June 2022 by the Microsoft Threat Intelligence Center (MSTIC), Polonium is a highly sophisticated, currently active hacking group, which appears to be exclusively targeting Israeli organizations for cyber-espionage purposes – they have not so far deployed sabotage tools such as ransomware or wipers.
Microsoft researchers have linked Polonium to Lebanon and assessed the group has ties with Iran's Ministry of Intelligence and Security (MOIS).
ESET’s findings, presented at the Virus Bulletin 2022 conference in late September and published on October 11, 2022, show that Polonium has targeted more than a dozen organizations since at least September 2021. Their victims include companies in engineering, information technology, law, communications, branding and marketing, media, insurance and social services. The group’s most recent actions were observed in September 2022.
Polonium has developed custom tools for taking screenshots, logging keystrokes, spying via webcam, opening reverse shells, exfiltrating files and more. Their toolset consists of various open-source tools, both custom and off-the-shelf, as well as seven custom backdoors:
- CreepyDrive, which abuses OneDrive and Dropbox cloud services for command & control (C&C)
- CreepySnail, which executes commands received from the attackers’ own infrastructure
- DeepCreep and MegaCreep, which make use of Dropbox and Mega file storage services respectively
- FlipCreep, TechnoCreep and PapaCreep, which receive commands from attackers’ servers
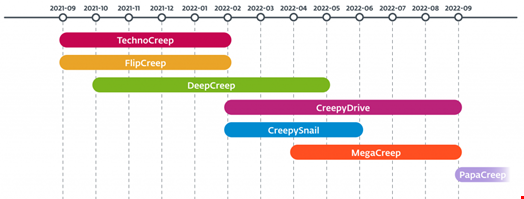
The most recent backdoor, PapaCreep, spotted in September 2022, was undocumented before ESET’s research was made public. It is a modular backdoor, breaking its command execution, C&C communication, file upload and file download functions into small components. “The advantage is that the components can run independently, persist via separate scheduled tasks in the breached system, and make the backdoor harder to detect,” BleepingComputer reported.
“The numerous versions and changes Polonium introduced into its custom tools show a continuous and long-term effort to spy on the group’s targets,” ESET said.
While ESET was unable to discover how the group gained initial access to the targeted systems, some of the victims’ Fortinet VPN account credentials were leaked in September 2021 and made available online. “As such, it is possible that the attackers gained access to the victims’ internal networks by abusing those leaked VPN credentials,” ESET added.
This correlates with previous findings by Microsoft, which reported in June 2022 that the group was using known VPN product flaws to breach networks.
“Polonium didn’t use domain names in any of the samples that we analyzed, only IP addresses. Most of the servers are dedicated virtual private servers (VPS), likely purchased rather than compromised, hosted at HostGW,” ESET said, making it harder to map the group’s activities.
