A critical vulnerability in the Rust standard library could be exploited to target Windows systems and perform command injection attacks.
The flaw was discovered by a security engineer from Flatt Security known as RyotaK. They named it BatBadBut, reported it to the CERT Coordination Center (CERT/CC) and published an analysis on April 9, 2024.
That same day, GitHub registered it as CVE-2024-24576, with a severity score (CVSS) of 10.0.
Decoding the BatBadBut Vulnerability
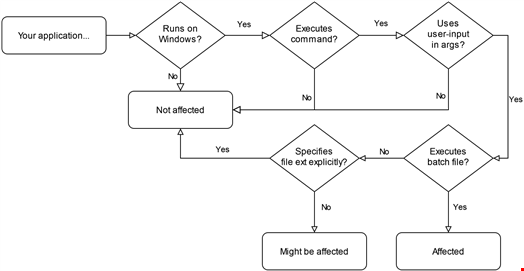
BatBadBut is a vulnerability that allows an attacker to perform command injection on Windows applications that indirectly depend on the ‘CreateProcess’ function when the specific conditions are satisfied.
RyotaK explained: “CreateProcess() implicitly spawns cmd.exe when executing batch files (.bat, .cmd, etc.), even if the application didn’t specify them in the command line. The problem is that the cmd.exe has complicated parsing rules for the command arguments, and programming language runtimes fail to escape the command arguments properly.”
The researcher said that because of this, it is possible to inject commands if someone can control the part of command arguments of the batch file.
In an advisory published on April 9, the Rust Security Response Working Group said it was notified that the Rust standard library did not properly escape arguments when invoking batch files (with the bat and cmd extensions) on Windows using the Command API.
“An attacker able to control the arguments passed to the spawned process could execute arbitrary shell commands by bypassing the escaping,” the advisory read.
High CVSS, Lower Risk?
BatBadBut has been attributed the highest severity score.
However, in their post, RyotaK suggested that the vulnerability's real-world exploitability might be lower than initially feared.
First, successful exploitation of BatBadBut only occurs when the following conditions are met:
- The application executes a command on Windows
- The application doesn’t specify the file extension of the command, or the file extension is .bat or .cmd
- The command being executed contains user-controlled input as part of the command arguments
- The runtime of the programming language fails to escape the command arguments for cmd.exe properly
Additionally, BatBadBut only impacts versions of Rust before 1.77.2 – no other platform or use is affected.
The high CVSS score comes from how such a score is attributed to a library.
“The user guide of CVSS v3.1 states that the CVSS score of a library should be calculated based on the worst-case scenario, and this is why the recent vulnerabilities for programming languages got high scores despite the requirement of specific conditions,” RyotaK explained.
The security researcher recommends recalculating the CVSS score based on the Forum Incident Response and Security Team’s (FIRST) implementation recommendations for software libraries.