Threat Intelligence (TI) has become a must-have weapon in the cybersecurity professionals arsenal, with a huge variety of TI sources available, from open source feeds to specialized commercial service providers. TI promises to enable users to “know their enemy”, while providing situational awareness of the threat environment and active threat actors.
In practice, however, it is primarily used tactically. TI is typically correlated in machine-readable form to provide context and distill volumes of information on threat actors and their Tactics, Techniques and Procedures (TTP’s) into a reactive detection signature. While this has marginally improved threat detection, TI’s full value proposition has not been achieved.
The problem with TI is that there is too much of it. Identifying which threats are relevant to an organization requires time-intensive, manual analysis and verification, and even then exists only in the realm of probability. With thousands of active threats, proactively identifying the ones that will affect an organization involves more luck, than skill.
Operationalizing TI by correlating it with operational activity data, on the other hand, takes the guesswork out of the equation. It also makes TI more of a predictive or strategic weapon, rather than a forensic tool.
As a result, TI can instead be used to inform security strategy and proactively ensure that an organization is prepared for common threats. It can also provide guidance for decisions on which technologies to deploy and how to deploy them, as well as how to detect and respond to specific threats.
Conducting Threat Assessments
Threat assessments are used to determine whether a threat is likely to target an organization, how the threat will used in an attack and whether effective measures are in place to protect against it.
This is rarely a precise science. Precision is desirable, but accuracy will suffice. For example, an organization that provides critical services to government does not need to reliably identify the specific state sponsored threat actor group that will target them. It is sufficient to be aware that in general, a range of state sponsored hackers pose a threat.
This insight is sufficient to analyze a cross-section of state sponsored actors and extrapolate commonalities in their TTPs to determine what security measures will be most effective to protect against them. Consider coastal settlements as an analogy. They do not build levees for a specific hurricane, but rather to protect against them in general and based on their threat assessments, they know to build levees and not earthquake proof buildings.
To conduct a threat assessment, an organization must consider the motive, intent and opportunity of threat actors. Are they targeting all organizations with a similar profile? In a similar geography? In a similar vertical? Does an organization have business relationships with partners that they are targeting?
By conducting a high level, consolidated analysis, it is possible to build several Threat Profiles with their associated TTPs. These profiles in turn can be used to determine security strategy.
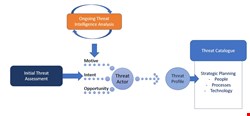
When an organization begins using threat intelligence strategically, it must be implemented as broadly as possible to construct an initial catalogue of threat profiles. Ongoing, new and emerging threats can be assessed and analyzed to verify and update these threat profiles.
Once threat profiles have been determined and associated common TTPs identified, they can be used to assess whether existing security measures are adequate or not.
For example, if the majority of nation state sponsored hackers utilize spearphishing to initiate attacks, are the correct preventative and detection technologies in the right places to mitigate and detect them? Has user awareness training on identifying phishing attacks been conducted? Are appropriate incident response playbooks in place to successfully contain phishing attacks? Any gaps can be used to determine strategic roadmap priorities, budget planning and where mitigating controls or additional monitoring resources should be allocated.
This can be a purely theoretical exercise that involves evaluating documentation and interviewing stakeholders. However, a better approach is to conduct a threat simulation. Using the TTPs that were identified during the threat assessment, it is possible to simulate each stage of a hypothetical attack. Would the indicators of compromise (IoC) be detected? Would lateral transfer and privilege escalation be detected? Would an attacker be able to gain access to critical information? Are the processes, technology and people in place to respond to such an attack? Who needs to be contacted in the event of a breach? Can breach notification time requirements be fulfilled?
Threat simulations help to vet and verify intended measures, and identify flaws and gaps proactively, rather than discovering them during a breach. Although threat simulations cannot predict if a specific threat actor will attack the organization, they can predict if an attack would be successful.
Without situational awareness, organizations must use whatever means at their disposal to protect against every possible threat. Of course, this is not feasible with limited resources.
Much like coastal towns most susceptible to hurricane flooding won’t spend on earthquake proofing, organizations should also focus on the most likely threats that target them. This can be accomplished using TI to gain a better understanding of the type of threats active in the wild, who they target, why and how.
While this may require manual analysis of TI, the investment will yield a valuable return in the form of better use of security budget and resources, as well as better protection.
