SSL is becoming increasingly important to the maintenance of private communications. Intelligence agencies' ability to tap communications links (such as GCHQ's Tempora program, and the NSA's relationship with US telecommunications providers) means that any message that is not encrypted is potentially readable. SSL provides such encryption; and despite NSA and GCHQ efforts to subvert encryption, SSL is still believed to be secure.
But problems with its use remain. SSL relies on the generation and exchange of session keys to encrypt each communication. The most common process is to use RSA to protect those keys. "This is an efficient key exchange approach, but it has an important side-effect: anyone with access to a copy of the server's private key can uncover the session keys and decrypt the conversation," explained Ristic in June.
And as Whit Diffie told Infosecurity in July, "If you organize things so that there are 'central' people (phone companies, bit websites) who can sell you out, they probably will." The RSA approach to securing the SSL keys involves just such a centralized approach.
"In the context of mass surveillance," wrote Ristic, "the RSA key exchange is a serious liability. Your adversaries might not have your private key today, but what they can do now is record all your encrypted traffic. Eventually, they might obtain the key in one way or another (e.g., by bribing someone, obtaining a warrant, or by breaking the key after sufficient technology advances) and, at that time, they will be able to go back in time to decrypt everything."
The favored solution is known as SSL with Forward Secrecy. "Given the increased importance of Forward Secrecy (FS) in SSL/TLS server configuration, SSL Pulse now tracks support for it among the servers in our data sample," Ristic announced yesterday.
Forward Secrecy does not use RSA-based key exchange, but instead uses the Diffie-Hellman ephemeral algorithm. Only the two parties involved in the communication can access the keys, and they are destroyed afterwards. So although communications could still be intercepted and stored, an adversary would need to crack the session keys for every separate communication. This is not currently believed to be realistic.
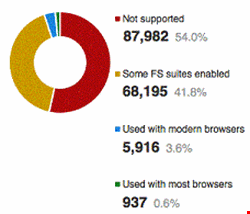
But the first results of SSL Pulse's new granular survey of Forward Secrecy usage shows there is much still to be done to ensure privacy in communications. "The results show that a large chunk of the servers (54%) does not use Forward Secrecy with any of the desktop browsers," announced Ristic yesterday. "However, a pretty large chunk (41.8%) does use it with some of the browsers. Only a small number support Forward Secrecy with modern browsers (3.6%), and an even smaller number (0.6%) support robust Forward Secrecy across most browsers."