
Rogue access points (APs) are unauthorized and unmanaged WiFi APs present inside corporate premises and connected to a corporate network. A rogue AP lacks the proper security controls provided for corporate authorized APs, and thus provides backdoor access to a corporate network for anyone connecting to the installed rogue AP. Further, rogue APs can be installed by a naïve employee (for convenient network access) or deliberately by an employee/outsider to execute malicious intent.
Once a rogue AP is installed on to the corporate network, a malicious outsider can connect to it from numerous places, such as parking lots or outside of the building premises. Also, a malicious employee/visitor who would typically have access to only a particular segment(s) of a corporate network can have easy access to other restricted segments if such segments suffer from rogue AP installation.
After connection to a rogue AP, a user can hack into a corporate network/network segment with malicious intent, such as disrupting network operations or accessing confidential data. As such, rogue APs provide a means of escaping the physical security of corporate networks. One can visualize a rogue AP as being analogous to an extended corporate Ethernet cable running into unintended places. Rogue APs are now widely acknowledged as one of the major WiFi threats by many leading WiFi infrastructure and WiFi security vendors.
Introduction of compact traveler APs, improvements in AP functions, and advancements in WiFi adapter drivers have vastly increased the landscape of rogue APs, which until recently was limited to relatively bulkier standalone physical AP devices that required to be plugged into the LAN port for network access.
Present-day rogue APs can be set up using a physical pocket-sized AP or via a software application on popular operating systems, such as Windows and Linux. Also, some of the rogue setups can now connect to corporate networks over WiFi where the capability exists.
Here is a list of interesting scenarios for rogue AP setup/installation that have evolved in recent times and require attention from corporate network administrators. All the listed scenarios are easily possible and the required devices or software for each of the scenario is readily available to anyone.
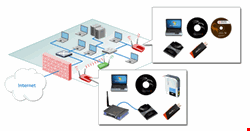
Compact, pocket-sized rogue AP device plugged into an Ethernet port: This rogue AP scenario, consisting of a pocket AP (easily available on the market) plugged in to the Ethernet port of corporate network, is interesting because the compact size of AP will make visual detection difficult. A compact-sized rogue AP device can be effortlessly brought into a particular location and easily hidden after installation.
Also, pocket APs have low power requirements and, hence, can be optionally powered from a battery also for long durations in cases where a power supply is not readily available near the Ethernet port. Introduction of pocket APs has truly benefited travelers but at the same time has increased rogue AP risks for organizations around the world.
Rogue AP device connected to corporate networks over a WiFi link: Instead of plugging into an available Ethernet port of a corporate network, in this scenario, the rogue AP device connects over a WiFi link. This circumstance is possible when a corporate network also has WiFi coverage. Hiding a rogue AP device is very easy in this example, as the device wirelessly connects to the authorized corporate network.
In addition, this scenario removes the constraint that requires an unused Ethernet port. However, a person installing the rogue AP device should know the required corporate WiFi credentials. To simulate this example, one can use a readymade rogue AP device with integrated WiFi access capabilities or, alternatively, a WiFi Ethernet bridge in conjunction with a regular AP device.
USB-based rogue AP device plugged into a corporate machine: A few vendors have also recently introduced a USB-type AP device, which has further promoted rogue AP setups. A USB-based rogue AP device is generally plugged in to a Windows machine with access to corporate network either through wired or wireless means. After plugging in, a machine’s corporate network access can be shared with a rogue device using software that comes with the USB AP.
USB-type rogue APs removes two typical constraints: the requirements of an unused Ethernet port and corporate WiFi credentials needed to set up a rogue scenario. Corporate endpoints are generally configured and authorized for access to the corporate network and, therefore, a USB rogue AP device plugged into one of these endpoints makes for a more stealth-like rogue scenario.
Software-based rogue AP running on a corporate Windows machine: The latest release of Windows operating system, Windows 7, has virtual Wi-Fi capability. Using this feature, a rogue AP can now be set up in the software itself on the plugged/embedded WiFi adapter of a corporate Windows 7 machine that has network access. Thus, no separate physical AP device is needed in this rogue scenario, making it even stealthier.
One can easily find readymade small utilities on the web to configure software rogue APs. With the increased adoption rate of Windows 7 into the corporate environment, the risk of setting up software rogue APs by malicious or naïve employees is also on the rise.
Software-based rogue AP on a corporate Linux machine: Various flavors of Linux operating systems are also capable of setting up a software-based rogue AP over the plugged/embedded WiFi adapter of the Linux machine. After the software AP is started on the Linux machine, it can be bridged with the organization network available on the machine to create a rogue scenario.
Even though Linux is not the most popular choice of operating systems for corporate endpoints, availability of Live CD/USB versions of various Linux varieties, such as BackTrack and Ubuntu, enable a malicious employee to boot Linux on their machine and setup a subsequent software-based rogue AP scenario without requiring a physical AP device.
Combating Rogue Access Points on a Corporate Network
A malicious user can use any one of the aforementioned scenarios according to his or her convenience to set up rogue APs and hack into a corporate network. All the described scenarios are stealthy in one way or another and thus require attention from corporate network administrators.
Proper security measures can be ensured by the deployment of a dedicated and all-round wireless intrusion detection/prevention system (WIDS/WIPS) solution that constantly scans corporate WiFi, 24/7, across all channels and correlates traffic on both the wired and wireless sides to identify and block all rogue APs operating on a corporate network.
Ajay Kumar Gupta is the acting tech lead, engineering, at AirTight Networks, a global provider of enterprise WiFi security and performance management products. He is a frequent contributor to some leading security magazines and AirTight’s blog.