
Are the vehicles we drive the next target for hackers? Wendy M. Grossman steers us around the risks
Anyone who has ever driven a car will have had no trouble imagining the terror of the drivers in the 2010 news stories about runaway Toyotas that could not stop accelerating until they ran out of gas or hit something. Many observers’ first thought was to blame the vehicle’s electronics. In the end, however, the electronic systems were cleared by the US National Highway Traffic Safety Administration (NHTSA), which concluded that the problem was mechanical, sometimes compounded by driver error.
The fear of a vehicle careening out of control is why so many people panic at the thought of Google’s self-driving cars – and it’s why the cars don’t hit the road without at least two Google staffers in charge. Yet a typical modern car, says security researcher Charlie Miller, who has been studying the matter recently, “has 10 to 30 computers, and they all have to talk to each other”. A luxury car may have as many as 70.
Similarly, Jim DeGraw, a partner with the global law firm Ropes and Gray, calls the Tesla or Chevy Volt “massive pieces of electronics attached to a drive train”. Even less futuristic cars are greeted on arrival at a repair garage with a cable that plugs into the standard diagnostics port to produce a diagnostic readout.
All of the aforementioned raises the very valid question: How vulnerable is that electronic device on wheels to being hacked? The answer is at least somewhat, if only theoretically – for now.
Open to Possibilities
“From a hacking perspective, it’s awesome”, says DeGraw. “You have controllers that control the gas mix, brakes, the information shared with others, how the car accelerates, what speeds it goes – it doesn’t take much mystery to think you could hack that and cause a safety problem for somebody, or capture information about people’s habits.” Besides all the things car manufacturers build in for their own purposes, he explains, “people are adding functions to the cars allowing insurance companies to record how fast you go and how far you drive in return for discounts.”
|
Modifying vehicles has a long history, but doing so has become increasingly inaccessible to average consumers. In the 1970s, sealed subsystems began superseding individually replaceable parts. In 1990, the Clean Air Act in the US forced new vehicles to include computer systems to monitor emissions, pushing the development of today’s sophisticated control systems. The upshot is that cars have become increasingly reliable at the expense of amateurs’ ability to fix their own vehicles. Jim DeGraw’s son, for example, is planning a project to fix up a 1950s or 1960s car – a very simple device that a teenager can work on. The family’s new Mazda, however, is well beyond any but a professional’s ability. The downside of securing cars against hacking, therefore, may be giving manufacturers greater scope to control who can work on the vehicles they make and how they source parts, locking out independent repair shops and hobbyist tinkerers alike. As long ago as 2001, both the US Congress and several state legislatures began considering proposals for ‘Right to Repair’ bills that essentially implement an automotive version of network neutrality; a bill finally passed in Massachusetts in 2012. Toyota Prius owners have long been famous for ‘hypermiling’ to eke every last mile out of their gas tanks, and it’s no stretch to think that people who enjoy tinkering with computers will want to do the same with the ones on wheels. As Robert Leale, the owner of canbushack.com, warned in his technical talk on the subject at last year’s HOPE event, the tools, as well as the risks in vehicle data hacking are expensive. This won’t stop the curious from studying vehicle systems, however; the OpenGarages project seeks to provide public access, documentation, and tools to do just that. |
There’s increasing interest in these possibilities. At the 2011 Black Hat security conference in Las Vegas, researchers Don Bailey and Matthew Solnik of iSec Partners demonstrated the hacking of a vehicle’s electronic key system to remotely unlock doors and turn on the engine. In 2012, real-life thieves in Europe implemented a two-step process by which they first bypassed a BMW’s intrusion alarm and then connected a reader to the on-board diagnostics connector to collect unsecured or easily decoded key codes to program a new key. A more sophisticated variant involves an electronic frequency scanner that tests remote door codes at high speed.
Either way, you need a blank key, and these are restricted in North America – but there’s enough financial motivation to inspire the creation of hacking tools to reprogram keys or kits to create new ones. This year, Canada’s REcon event lists talks on “hot-wiring of the future” and OpenGarages, a project to open up the internals of vehicular computer systems to the community at large.
Similarly, security consultants are trying to get a jump up on the potential opposition. Vlad Ovtchinikov and Rogan Dawes, analysts at UK-based SensePost, have been pondering the possibilities that will derive from integrating Android and other mobile devices.
“If someone can gain access to your Android”, says Ovtchinikov, “if you are 3G or Wi-Fi enabled, the Android within the car can communicate with the rest of the world. Besides the usual risks, that adds the potential for tracking your car, eavesdropping on conversations, and compromising any system it controls.” Something like triggering an airbag or suddenly blasting the radio volume may sound small beer, but these scenarios could pose serious danger if you’re going full-speed.
Preliminary Results
Research in this area is difficult for a couple of reasons. For one thing, auto manufacturers publish few details. For another, it’s expensive. Anyone might risk bricking a three-year-old, out-of-warranty iPhone, yet they might balk at risking a $5,000 repair on a $40,000 car.
The state of the art is data published in 2010 and 2011 by a team of 10 researchers from the University of California at San Diego (UCSD) and the University of Washington. The bad news is that cars definitely have vulnerabilities.
Manufacturers have understandably viewed protecting the safety of occupants of a two-ton chunk of metal hurtling down a highway at 70 miles an hour when a component fails as more urgent than imagining an evil adversary intent upon perverting a car’s software. The group showed it was possible to use the vehicle’s diagnostic port to control its computers. Inserting a CD with specially crafted MP3 files that, when played, would inject malicious code, the team was able to remotely lock the brakes, engine, and windows, control the radio, heat, horn, and windshield wipers, and even change the speedometer display.
In later work, the same researchers studied attacks that could control these systems remotely. They declined to identify the make and model of the car they studied, on the basis that many of today’s auto manufacturers are really system integrators that assemble their vehicles out of parts and subsystems built by a complex ecosystem of partners and suppliers.
The good news is that car manufacturers have taken their work seriously, according to Stefan Savage, a computer science and engineering professor at UCSD and member of the research team.
“I have nothing but spectacular things to say about the engineering staff of all the companies”, he reveals. “Even engineers with responsibility for individual components were not used to thinking of them being abused and that they might be capable of doing other things they hadn’t anticipated. Having put together a demonstration and source code was critical to making believers of them.”
Savage continues: “I’ve been impressed at the internal calculation management made that this, in fact, was something quite important for them to take seriously. It happened to overlap the Toyota unintended acceleration issue, and that really drove the issue home to manufacturers that there were huge potential brand damage issues here.” The UCSD professor notes that the research team was in contact with regulators and the automotive industry before publishing anything, and says that since publication of the papers, manufacturers have hastened to fix or improve the things they could, and are redesigning the next generation. The team has also declined to publish the tool they wrote, CarShark.
|
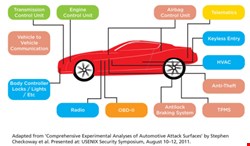
The computers inside a modern car monitor and control all aspects of the vehicle’s operation – from fuel delivery, spark timing, and emissions systems to engine load, airbags, brakes, door locks, and tire pressure (see Graphic). These computers, known as electronic control units (ECUs), include tens of millions of lines of code, and are interconnected via an electrical bus, usually Controller Area Network (CAN), first released in 1986 by Robert Bosch GmbH. As the first of two papers by Savage’s team explains, there are several types of physical access to these ECUs. A standard diagnostics port mandated for all passenger cars – OBD-II in the US since 1996, EOBD in the EU – provides direct access to the car’s key communications buses. The port may be accessed via dedicated handheld scanning tools, but increasingly manufacturers provide pass-through devices that plug into the diagnostics port and connect to a Windows-based laptop via USB or Wi-Fi. Mechanics then use software running on the laptop to query or program the ECUs. The laptops themselves, often internet-connected, may be compromised like any other Windows machine. Other physical access vectors include the cables to external chargers for electric vehicles and the CDs, USB sticks, and iOS/Android devices that owners can plug into the vehicle’s entertainment systems. The latter, in turn, increasingly also connects to the CAN bus to support functions like hands-free access or to provide a way of updating the ECU’s firmware. For short-range wireless access, cars may have Bluetooth or Wi-Fi, or dedicated systems such as RF-based remote keyless entry, RFID built into keys, or sensor-based tire pressure monitoring systems that also transmit over RF channels. For longer-range wireless, vehicles or attached systems may access broadcast media such as GPS, satellite radio, the FM subcarrier band-transmitted Radio Data System (RDS) and Traffic Message Channel signals. Plug-in interfaces for Android or iOS devices add the 3G, Wi-Fi, and Bluetooth wireless interfaces common to those devices, as well as the apps they bring with them. (Says Rogan Dawes: “You’re taking a rigorously developed system and plugging in Typhoid Mary.”) Finally, car manufacturers are enviously eying mobile’s app ecosystem. In May 2013, Juniper Research estimated that the in-car app market will be worth $1.2 billion by 2017. Trials are also ongoing for vehicle-to-vehicle (V2V) and vehicle-to-infrastructure communication, although these remain some way off. |
All of that care is salutary as far as the automotive industry is concerned but, as Charlie Miller points out, it’s hard for fellow researchers to replicate their results. This replication is what Miller has been working on; he expects to publish the results later in 2013 (see Update).
Declining to go into detail before publication, he says, “A big part is to open up the previous research to provide more information and more insight”.
|
Shortly after the writing of this article, researcher Charlie Miller – along with colleague Chris Valasek – unveiled the research results he hinted to us about earlier this year. The two researchers wrote code that allowed them to control various electronic features of a 2010 Toyota Prius and 2010 Ford Escape, including the vehicles' steering, braking and acceleration. The data was shared with fellow researchers at last month's DEF CON event in Las Vegas. Billed as the creation of a research tool into the area, Miller told Dark Reading: "This addresses a problem that doesn't really exist yet but we're afraid will, very soon. We want to get ahead of the curve." |