Credential stuffing is a type of cyberattack where malicious actors use bots to test stolen username and password pairs at scale. Because people tend to reuse passwords across websites, the method enables hackers to identify valid login data. These credentials can then be monetized via resale or used for various types of fraud, e.g. using influencer accounts with good reputations to conduct crypto scams.
A successful credential stuffing attack can do significant financial and reputational damage to your business. And while traditional security tools like WAFs can mitigate unsophisticated attacks with relative efficiency, it’s a different story when bot operators are willing to spend big money.
In this article we will explore what it might look like when a motivated attacker goes after your user accounts.
A Heavily Distributed Credential Stuffing Attack
The threat research team at DataDome, a cybersecurity company specializing in bot protection, recently observed an edifying attack on the login endpoint of a popular video gaming platform. The attackers didn’t spare their efforts:
- The attack lasted for ~4 days
- The attackers made nearly 108 million malicious login attempts
- They leveraged more than 91 million different IP addresses located all over the world
- Each IP address made only 1.18 login attempts on average—very hard to detect
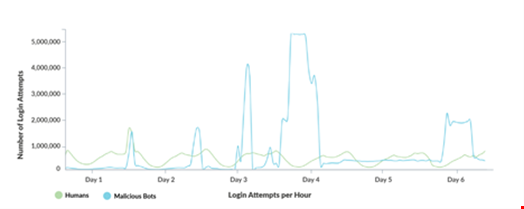
Graph one shows the timeline of the attack. The green line shows human login attempts over time, while the blue line shows the malicious login attempts conducted by bots.
We can observe five major spikes of malicious traffic, including two spikes where the attacker made more than four million malicious login attempts per hour for several hours.
More Than 91 Million IP Addresses
The nearly 108 million malicious login attempts were made with over 91,340,141 distinct IP addresses. That means, on average, each IP address made only 1.18 malicious login attempts. Against this level of distribution, traditional rate limiting policies are totally powerless.
Furthermore, the IP addresses used in the attack were mostly “clean”. By that, we mean that the majority of them had not been involved in any significant malicious activity against any DataDome customers in the week preceding the attack.
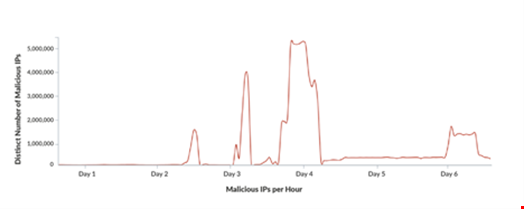
Graph two shows the number of distinct IP addresses used by the attacker over time. Since each IP address makes only 1-2 login attempts, this graph is highly correlated with graph one.
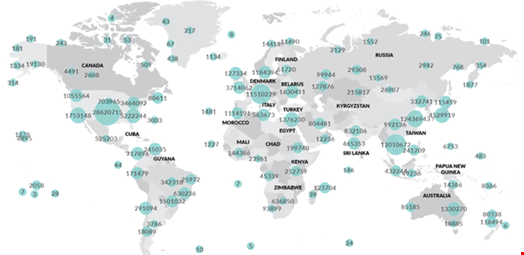
The map below indicates the number of malicious login attempts per country. As we can see, the attackers used IP addresses from all over the world. This means that the attacker had access to a significant pool of clean IPs located in different countries, ranging from the US and the UK to China, France and Germany.
Most importantly, the attacker had access to clean residential IP addresses, the same type of IP address real humans use to browse the internet.
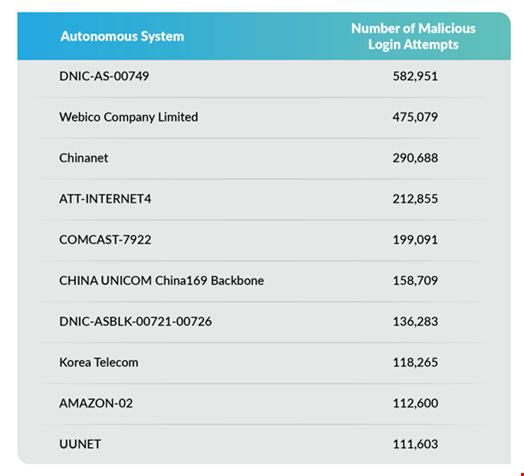
We can see that the attacker had access to residential IPs from legitimate internet service providers all around the world, for example these American providers:
- AT&T
- Comcast
- Verizon (UUNET)
Tracking Malicious IP Addresses
IP addresses are often shared by many users, which can include both bots and humans. IP addresses can also be reassigned. To avoid blocking real users (aka false positives), it is therefore important that the bot protection system’s IP reputation data is continuously updated.
Thanks to its real-time detection engine, DataDome can easily tag IP addresses to observe and study their activity across all customer websites protected by the solution.
Graph three below shows the number of malicious requests coming from a subset of the IP addresses that were used for the attack we are analyzing. We have included data from four different DataDome customers that were all targeted by the same IP addresses.
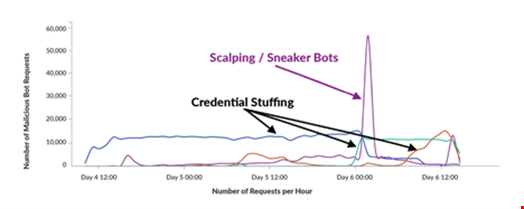
Many of these IPs are still conducting credential stuffing attempts on the same video gaming platform. They also continue to target other DataDome customers with credential stuffing attempts.
Furthermore, in addition to credential stuffing attacks, some of these IP addresses have also been used by sneaker bots for scalping attempts during “sneaker drops”, i.e. releases of limited-edition sneakers.
How to Avoid Becoming a Victim of Credential Stuffing Attacks
As our example demonstrates, fraudsters are sometimes ready to invest considerable human, technical, and financial resources in distributed credential stuffing attacks:
- Advanced attacks are highly distributed
- Bot operators have access to vast pools of high-quality IPs
- Traditional mitigation techniques, such as rate limiting, would not have worked.
If your user accounts are valuable, would your current security system stand up to the challenge?
To efficiently mitigate massive attacks, a real-time bot detection solution is crucial. Rules-based tools are powerless against attackers who have access to a huge pool of IPs.
An effective bot protection solution must leverage the full spectrum of bot signals:
- Client-side signatures, including browser/JS fingerprints
- Server-side signatures, such as HTTP headers and TLS fingerprints
- Behavioral signals, such as mouse movements, touch events, and sensors
- Reputational signals per IP and session, including proxy detection
To stay safe against distributed attacks, it’s also extremely important to choose a bot protection vendor with a broad customer base and deep knowledge of the current threat landscape. Remember, in the credential stuffing attack detailed above, thousands of the IPs involved were later used to conduct different types of attacks on other enterprises.
Protecting hundreds of e-commerce sites and mobile applications all around the world enables DataDome to deeply understand how attackers operate and to efficiently protect all customers.

