Microsoft OneDrive remains the most exploited cloud app for delivering malicious content, a sceptre held firmly since November 2021 (11 months in a row!), according to the Netskope Threat Labs Report – September 2022. This is despite the impressive growth in the number of cloud services abused for malicious purposes.
New cloud services are joining the target list regularly, as threat actors consider them a powerful weapon that enormously simplifies the execution of a malicious campaign. This trend has been consistently building. In January 2022, the top three exploited cloud apps – OneDrive, Sharepoint and GDrive – accounted for 85% of cases. In September 2022, the aggregated percentage of the same three apps dropped to 30%, meaning the other 164 distinct cloud apps that Netskope detected that distributed malicious content accounted for 70% in the same month.
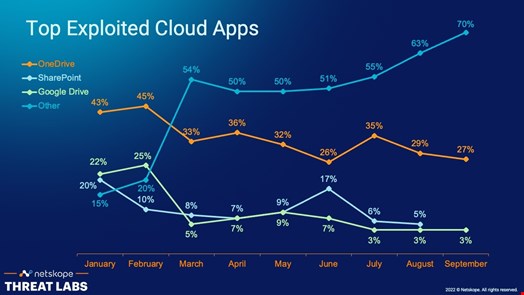
Even if this fragmentation means attackers constantly exploit new cloud apps, Microsoft remains their preferred weapon. However, the Microsoft 365 platform is not the only Microsoft service being regularly exploited by threat actors, despite the usual suspects, including OneDrive, SharePoint, and even Azure steadily ranking at the top of this unwelcome chart. GitHub and LinkedIn are also part of the Microsoft family, two services well-known and trusted by millions of users and organizations worldwide and have quickly gained popularity among attackers. Case in point, LinkedIn is now the most impersonated brand for phishing attacks.
In any case, even with plenty of choice for the attackers inside and outside the Microsoft app ecosystem, Microsoft 365 still gets the lion’s share. Attackers can choose to compromise a legitimate account and abuse multiple services to launch attacks from a trusted location, targeting that organization or even an external objective. Similarly, they can spin up their own accounts and use internal apps to deliver malware, host phishing pages, bait documents, or even command and control infrastructure.
In both cases, attackers increase their chances of bypassing security gateways (this explains why cloud accounts are a growing target for opportunistic or state-sponsored threat actors) and simplify the preparation and staging of their attack, given that the Microsoft 365 environment offers so many ready-to-use tools. The same logic applies to other platforms, such as Google Workspace.
Less Common Applications Are Still Exploited
One of the consequences of the wide availability of tools inside a compromised cloud account is that even the less commonly-used applications are often abused. One example is Microsoft Sway, which can be weaponized to deliver malware and phishing pages. Sway allows the combination of text and media to create a presentable website, which means that the attackers can unleash their creativity to build professional, realistic-looking and more legitimate phishing pages. These can look much more convincing than the ones built with immediately available tools such as Microsoft Forms or Google Forms. Sway also allows users to embed documents in the pages, facilitating malware delivery.
The exploitation of Sway is not a novelty. In the first quarter of 2020, a massive campaign called PerSwaysion was unearthed, having been active since mid-2019. It targeted 156 high-ranking officers in small and medium financial services companies, law firms and real estate groups, and was characterized by the abuse of Microsoft Sway (as well as SharePoint and OneNote) to redirect victims to actual phishing sites.
Multiple Ways to Exploit Virtually Any Service
Even the most commonly-used applications, such as OneDrive, can be exploited more subtly by state-sponsored and opportunistic threat actors. In January 2022, a new cyber espionage malware was discovered called Graphite and attributed to APT28, a threat group with nexus to Russia’s General Staff Main Intelligence Directorate (GRU). This malware leverages OneDrive as a command and control server via the Microsoft Graph API and seems to be particularly profitable for attackers, given that a new campaign by the same threat actor with the same malware has been recently unearthed. This new campaign is particularly noteworthy, not only because OneDrive is abused for both delivery and distribution and command and control (further proof of the flexibility of OneDrive), but also because its installation is triggered when the user starts a weaponized document in presentation mode and moves the mouse.
Protecting Against Exploited Cloud Services
There are a few steps that organizations can follow to mitigate the risks of cloud apps embedding malware or phishing pages:
- Firstly, educate users to recognize rogue cloud instances weaponized to deliver malicious content. There are always misplaced details (such as the domain or some layout glitches in the content of the page) that can raise alarm bells.
- Secondly, make sure your own cloud accounts are not compromised. Implement multi-factor authentication and a security posture management solution, which can mitigate the risk of misconfiguration exploitable by the attackers.
- Thirdly, implement a Cloud Access Security Broker (CASB) to detect initial account compromise and post-exploitation anomalous activities.
- Finally, enforce security at the access edge in terms of adaptive access control, DLP and threat protection, applying more restrictive policies for unmanaged applications or unmanaged instances of corporate applications.
As cloud applications are increasingly the most attractive attack vector for threat actors, it is essential that businesses gain greater visibility over their cloud infrastructure to identify and mitigate threats before serious damage is inflicted.
