Despite the increased focus on application security in the last few years, cyber-threats are increasing in volume, sophistication and impact. To help companies defend against them, OWASP, a non-profit that aims to raise awareness about application security, compiles a Top 10 List of the most severe threats. In 2021, OWASP undertook a major update of the list to reflect new risks opened by the flexible models that are driving work today, and as part of these changes, introduced several new categories, including two that focus on the changing nature of modern application design principles and software development lifecycles and the security holes they can open if left unchecked.
What are these categories, and why are they relevant?
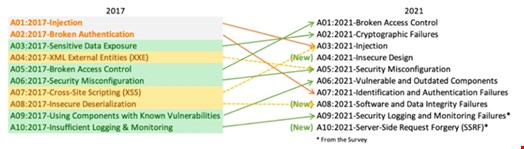
Cryptographic Failures: Continue to Expose Sensitive Data
According to OWASP, cryptographic failure is the second most critical security vulnerability for applications. This should come as no surprise. All too often, businesses fail to take rudimentary steps to adequately protect their sensitive data from exposure through a lack of, or poorly implemented, encryption technologies.
The impact of exposing sensitive data can be devastating for a business and can lead to loss of customer confidence, reputation damage and legal exposure. Moreover, data privacy laws such as GDPR, HIPAA and CCPA can stipulate stiff fines for breaches.
In this category, OWASP identified 29 common weakness enumerations (CWEs) and called out the use of hard-coded passwords in applications and broken or risky crypto algorithms as two of the most notable. Unfortunately, many organizations still use cryptographic algorithms that are proven to be risky to protect their data at rest and in transit.
The obvious first step is not to store sensitive data longer than you have to – if you don’t have the data, it can’t be stolen! Of course, when you must hold or share sensitive data, don’t keep/send it without encryption. Enforce encryption for all data at rest and in transit by default. Make sure to use strong encryption – modern SSL algorithms, protocols and keys. Further, best practice dictates the use of authenticated encryption to ensure data confidentiality and authenticity. Also, check your configuration using the Qualys SSL Labs A+ certification tool.
Vulnerable and Outdated Components: A Bigger Threat Now
It should go without saying that using vulnerable and outdated components is an application security risk. In 2017, it ranked ninth on the OWASP Top 10 List. In the 2021 update, it jumped to the sixth spot, based on the data and the number of flaws reported.
Moreover, security professionals polled by OWASP see it as the second biggest threat they must manage. It’s tough to track all the versions of the components in use and stay abreast of which are vulnerable, unsupported or out of date. It isn’t getting any easier.
While this is a problem that will never go away, it can be mitigated. Obviously, businesses should not need to be told only to use official sources and versions for software components – and ensure that software is always signed to prevent modified and malicious components (although this is not a guarantee of security – SolarWinds!)
Similarly, businesses will have to do a better job of continuously inventorying the components in their environments and checking for disclosed vulnerabilities and new CVEs. While there are tools that can help with this – e.g., OWASP Dependency Check – there may be a need for manual checks as well. It’s important to establish an application lifecycle plan to help monitor, apply updates and check configs regularly to stay ahead of the curve.
Key Takeaways
Despite all the increased focus on application security in the last few years, cyber-threats are increasing in volume, sophistication and impact. The OWASP Top 10 covers the most severe threats, but it doesn’t make it any less serious if you are hit by an attack not listed. You should treat the list as a starting point. Of course, you need to adopt what’s relevant and prioritize your defense strategy – think about what changes you can make to mitigate the most critical vulnerabilities.
A good first step is to deploy a web application firewall. WAF vendors work hard to publish signatures and techniques that will mitigate the effect of the attacks on the Top 10 list (and others) and safeguard your assets.
You should go further. If you rely on third-party code, ensure it’s from trusted sources. If you use home-grown code, review it thoroughly and test it throughout its lifecycle. Define and enforce authentication, authorization and encryption across the board. When you accept data, validate all input to prevent malicious code execution. This is easily done by deploying web application firewalls.
Overall, protecting apps has never been easy. The OWASP Top 10 list, along with good security practices and the right solutions, can make it easier to enforce a better security posture.

