Why Proactive Data Protection is Better Than Waiting for the Inevitable
As sophisticated cyber-attacks increasingly target SaaS data, both vendors and customers are pushing to increase investments in SaaS security. Vendors are dedicating substantial resources to product development, incident communication and customer outreach. Simultaneously, many customers are elevating SaaS security conversations to their CISOs and Information Security (InfoSec) teams. Others are still considering their options and their risk appetites.
While these immediate investments are successfully mitigating many current threats, the emergence of new attack vectors continues to increase both the probability and the financial cost of security incidents targeting SaaS data. Consequently, the administrative effort and security tooling investment necessary to maintain a secure posture will continue to rise as SaaS environments scale - particularly as the adoption of agentic AI grows.
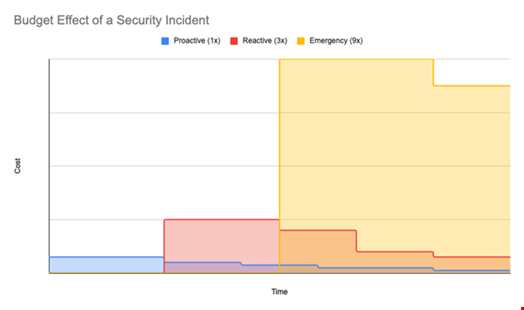
The swift and sweeping shift in budget allocation post-incident, flipping from underspending to prioritizing security, is referred to as the budget effect of a security incident. The 2025 IBM Cost of a Data Breach Report found that 49% of organizations would increase emergency security investment following a data breach.
Surprisingly, this is 22% lower than the 2024 IBM report, which may be attributed to organizations taking a more proactive approach to security investment, reacting decisively when their peers have been subject to visible breaches. The figure below depicts how the cost of waiting until a security incident occurs far exceeds (greater than 9x) the cost of proactive data protection, or even the reactive approach (greater than 3x) when peer organizations have suffered data loss.
The SaaS Admin’s Dilemma
SaaS administrators are now at the forefront of defending some of the most critical data an organization holds. However, they have limited time and expertise for security and can’t do it alone. SaaS security has a steep learning curve, and prioritizing risks can be daunting. SaaS administrators need support from InfoSec in the form of cybersecurity expertise, risk prioritization, and budget allocation.
This budget allocation is often overlooked when a project is in the proof-of-concept or early stages of delivering on a business need. However, as reliance on the platform grows, so do the non-functional requirements — especially those related to confidentiality, integrity, and resilience.
Bridging the Gap
This “InfoSec↔SaaS Divide” series has explored strategies to secure SaaS environments, the necessity of data resilience, and the operational bridge built by the NIST Cyber Security Framework (CSF) and Agentic AI. However, even the most robust security initiatives often stall at the budget approval stage. Executives frequently don’t appreciate that SaaS security is a partnership and assume that data security is fully managed by the vendor, viewing additional protection as unnecessary. To secure funding, IT security leaders must shift the conversation from reducing risk of security incidents to protecting value and improving operational efficiency. This final article presents the financial arguments and regulatory context necessary to justify the budget for true SaaS Confidentiality, Integrity, and Resilience, thereby bridging the gap between technical risk and financial reality.
The Cost of Waiting vs. The Cost of Preparing
Many organizations underestimate their dependence on SaaS and under-invest in applying the NIST Cyber Security Framework to protect critical SaaS data. It is important to strengthen Identity and Access Management (IAM) and secure connected apps, including IP allow listing. Relying solely on perimeter protections provided by SaaS vendors and IAM solutions neglects the need for defense-in-depth as articulated in the previous article.
Organizations that wait until an incident occurs to bridge the InfoSec↔SaaS divide find that the damage, disruption, loss, and recovery time far exceed the cost of proactive SaaS data protection. They often lack the necessary information to determine what occurred, and in some cases, their data is never recovered. Disruptions result in lost revenue, share price impacts, negative media attention, supply-chain contagion, and severe regulatory penalties.
The budget effect is a simple yet painful economic reality: a proactive, planned project is always going to cost less to implement than a rushed, emergency initiative designed to make up for lost time after a disaster. The cost of a breach is a massive hit that necessitates emergency security investment at a premium, whereas a proactive approach is a predictable operational expense. Executives and shareholders prefer predictability. A reactive approach may eventually provide them with a greater level of confidence than just waiting, but compressed timelines will always drive costs higher.
Investing in SaaS Data Security
The infrastructure layer of SaaS platforms is built to be highly resilient and secure. However, this level of security is just the baseline; it rarely provides the full security suite. While vendors protect their platform and provide configuration options and security add-ons, it is up to each organization to decide what fits their risk appetite.
Critical capabilities, such as Single Sign-On (SSO), advanced encryption key management, extended audit log retention, premium granular backup with precision repair, and real-time event monitoring, frequently require higher licensing tiers or are sold as premium add-ons. These features have an inherent cost to provide, maintain, and optimize as a premium capability. Consequently, the assumption that “it’s all included” typically leaves organizations operating with a “standard” security posture that is insufficient for enterprise compliance needs.
As the adage goes, the best time to plant a tree was 20 years ago; the next best time is today. The same is applicable to your security and resilience tooling. It needs to be implemented, functioning, and tested well before an incident occurs. This is vital even before we consider how the world is changing to embrace automation and agentic AI, technologies which will significantly strengthen SaaS defenses and amplify security savings, even as they simultaneously increase threat vectors (in the hands of cyber criminals).
The Invisible ROI: Regulations as a Roadmap
The goal is to leverage the headlines for insight rather than becoming the news. When executives ask, “Could that happen here?”, the answer has historically been “probably not.” However, the threat landscape has changed. It’s no longer a question of IF it will occur, but WHEN. The answer is “yes,” and the discussion must immediately shift to the precise investments required to mitigate or minimize the damage. Capitalizing on the lessons learned by others is smart business, while repeating their mistakes is negligence.
Cybersecurity regulations like the EU Digital Operational Resilience Act (DORA), NYDFS Cybersecurity Requirements (23 NYCRR 500), and NIS2 codify lessons learned from past incidents and serve as a powerful justification for budget. These frameworks provide a clear roadmap that, when followed using automated tools, offers significant cost savings and efficiency gains compared to unsustainable manual compliance methods:
- Robust Risk Management: Understand, categorize, and mitigate risks that could cause security exposures or operational interruptions. This includes managing security configuration and performing annual risk assessments. Leveraging automation and Agentic AI to control security configurations, compute risk scores, and enhance threat monitoring can be done in a fraction of the time compared to manual methods.
- Data Classification: Identify and label personal and other valuable information assets. This is foundational to applying the right protection, such as encryption and the Principle of Least Privilege (PoLP). Automation and AI/ML can accelerate data classification and related tasks significantly, and more comprehensively.
- Continuous Monitoring: Implement mechanisms to promptly detect, manage, and learn from anomalous activities. Continuous monitoring leads to faster time-to-detection, and it is now possible to respond to specific threats in real-time using automation and AI Agents.
- Business Continuity and Disaster Recovery (BCDR): Maintain plans and regularly test the ability to recover from backups within defined RTO & RPO. Production systems must be separated from recovery systems, a requirement that demands a budget for specialized backup solutions. The ability to precisely repair lost or corrupted SaaS data from backup is essential for maintaining availability and integrity, and ensuring uninterrupted business operations.
- Incident Response: Prepare the processes, people, tools and data necessary to detect and handle security events in a timely manner, while minimizing damage.
- Compliance Evidence: Produce documentary evidence supporting compliance attestations. Generating this evidence automatically using specialized technical solutions for risk scoring and one-click reporting can cut audit documentation time from weeks to days, and improve the comprehensiveness and consistency of audit documentation.
Conclusion
Postponing investment in SaaS security ultimately incurs higher costs in the long run. Proactive data protection and security investment is more cost-effective than reactive measures, and organizations should analyze how to monetize the efficiencies gained through risk management, increased speed of innovation, or the avoidance of additional staffing required for manual operations.
Regulatory compliance is no longer a check-the-box exercise, but a blueprint for the baseline of security and operational continuity. Invest strategically in automated resilience that meets these requirements while delivering tangible operational efficiency and protection against existential risk.
How long will you wait to prioritize investing in SaaS data security before a loss or breach occurs? To avoid the budget effect of a security incident, build a business case for investing in SaaS security today by taking these three steps:
- Quantify the financial risk: Put a dollar figure on a 4-hour outage of your SaaS system to justify resilience tools and a significant data breach.
- Audit your waste: Calculate the cost of manual log reviews, configuration checks, risk assessment, and audit reporting to justify the ROI of automation.
- Invest in automation: Use AI to scale protection and demonstrate provable compliance to your stakeholders.
By proactively implementing and automating key cybersecurity controls, with consideration for the specifics of SaaS environments, successfully bridging the InfoSec ↔ SaaS divide, organizations can reduce risk and avoid the long-term, detrimental financial ramifications of an incident.



