In March 2017, Fujitsu Cyber Threat Intelligence uncovered a newly developed remote access tool referred to by its developer as ‘Dark RAT’ – a tool used to steal sensitive information from victims. Offered as a Fully Undetectable build (FUD) the RAT has a tiered price model including 24/7 support and an Android version. Android malware has seen a significant rise in interest and in 2015 this resulted in the arrests of a number of suspects involved in the infamous DroidJack malware.
More recently, our partners at Checkpoint identified adware on the Google Play store which was downloaded by over 10,000 victims. This offers insights into the risks associated with mobile malware, and the convergence of mobile threats.
Tiered Pricing – Competitive Pricing Models
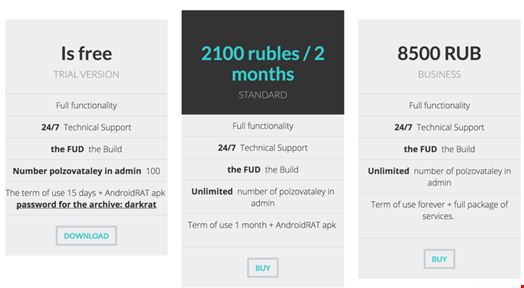
Dark RAT comes with a three tier pricing model which includes both a paid and a trial version. These include varying degrees of functionality in terms of administration and the Android RAT APK.
Feature Rich! Just Another RAT
Some of the features included with the RAT are similar to most available RATS which include:
? Browser credentials
? Keylogging capabilities
? Steam credential theft
? Skype user credentials
Whilst these features are not unique, they are effective, and as observed with other low level actors, using a method as simplistic as remote access trojans to compromise victims works.
These actors are commonly known as average attackers and use commodity malware to attempt to compromise victims. Although not unique to this chart, some crossover does occur but in the case of commodity malware this comes under an average attack.
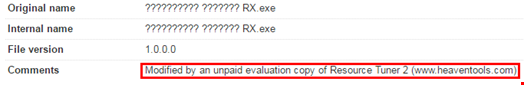
Some of these capabilities are shown by the developer of the RAT. Additionally the RAT, whilst still at version 1.0, appears to have been developed using an unpaid evaluation copy of Resource Tuner from www.heaventools.com according to metadata contained within the builder.
Scope of Victims
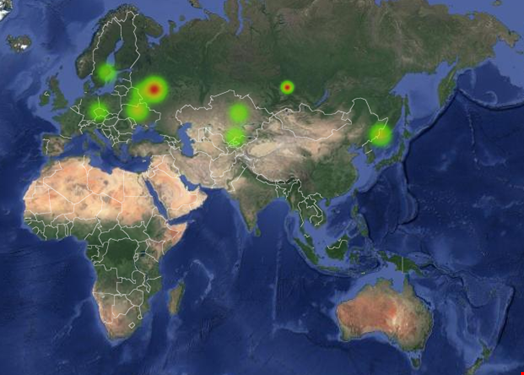
Some of the victims included by location were:
• Russia
• Ukraine
• Sweden
• Czech Republic
• Kazakhstan
Summary
As discovered in November 2016 when Fujitsu Cyber Threat Intelligence analyzed and reported a significant operation affected Middle Eastern businesses using KeyBase, we continue to observe similar threats. Although remote access trojans may not attract the same level of attention as Apex attackers, they cannot be disregarded simply because of the level of complexity, or lack thereof.
In today’s threat landscape, organizations can no longer afford to be complacent when it comes to security. It needs to be top of the boardroom agenda. By implementing an effective security education program alongside a strong threat intelligence system and incident response plan, an organization can combat today’s cyber-criminal networks and protect their data assets.
