Ransomware activity increased in 2023 compared to 2022, according to Google-owned Mandiant.
This is despite broadscale law enforcement operations against prominent ransomware groups, including ALPHV/BlackCat.
Mandiant shared ransomware research findings in a new report published on June 3, 2024.
The threat intelligence firm observed a 75% increase in posts on ransomware groups’ data leak sites (DLS) in 2023 compared to 2022.
In total, victims on DLS spanned more than 110 countries.
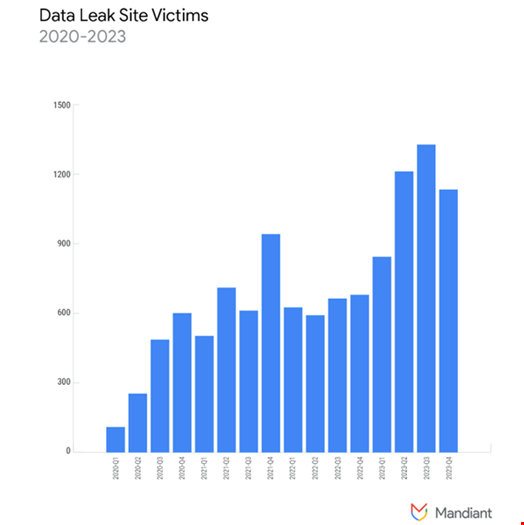
These observations are consistent with other reporting, including a Chainalysis report showing that over $1bn was paid to ransomware attackers in 2023 – a record.
“This illustrates that the slight dip in extortion activity observed in 2022 was an anomaly, potentially due to factors such as the invasion of Ukraine and the leaked Conti chats,” the Mandiant researchers wrote.
New Groups and Partnerships Drive Ransomware Activity
According to Mandiant, the current resurgence in extortion activity is likely driven by various factors, including:
- New entrants
- New partnerships between groups
- Ransomware service offerings by actors previously associated with prolific groups that had been disrupted
Although two of the most established ransomware families, ALPHV/BlackCat and LockBit, were the most frequently observed in 2023, Mandiant also noticed an increased diversification of the ransomware landscape, with 50 new ransomware variants. This is approximately the same number as in 2021 and 2022.
Read more: ALPHV/BlackCat Site Downed After Suspected Police Action
However, the proportion of new variants compared to families increased, with around one-third of new families observed in 2023 being variants of previously identified ransomware families.
“This could suggest that threat actors are using their time and resources to update pre-existing ransomware families rather than creating new families from scratch,” Mandiant wrote.

Finally, Mandiant found that threat actors increased their reliance on remote management tools in ransomware operations.
These tools were used during approximately 41% of intrusions in 2023 compared to 23% of intrusions in 2022.
