The potential for cybercriminals to use AI chatbots to create phishing campaigns has been cause for concern and now it has been found to be almost impossible to detect AI-generated phishing emails, according to email security provider Egress.
AI detectors cannot tell whether a phishing email has been written by a chatbot or a human in three cases out of four (71.4%), according to Egress’ Phishing Threat Trends Report, published on October 2.
The reason for this is due to how AI detectors work. Most of these tools are based on large language models (LLMs), therefore their accuracy increases with longer sample sizes, often requiring a minimum of 250 characters to work.
Almost half (44.9%) of phishing emails do not meet the 250-character requirement and a further 26.5% fall below 500, meaning that currently AI detectors either will not work reliably or will not work at all on 71.4% of attacks.
HTML Smuggling Revealed as the Top Phishing Obfuscation Technique
In the report, Egress researchers also found that human-generated phishing campaigns are getting harder to detect, with a 24.4% jump in obfuscation techniques which were integrated in over half (55%) of phishing emails in 2023.
These techniques have also grown in sophistication, with almost half (47%) of phishing threat actors deploying two obfuscation layers and less than one-third (31%) using only one technique.
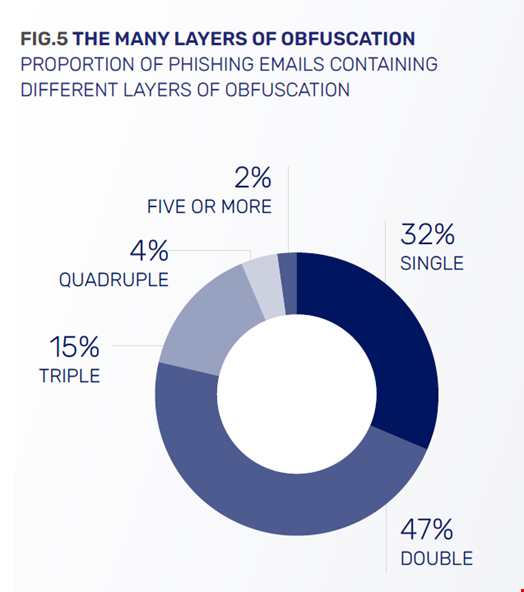
The most popular technique is HTML smuggling, which consists of exploiting legitimate HTML5 and JavaScript features to encode and embed malicious code within HTML files or web pages.
Additionally, Egress found that 34% of mail flow can be categorized as ‘graymail,’ which the company describes as “bulk but solicited emails such as notifications, updates, and promotional messages.”
These create a flood of emails that makes the work of phishing detectors harder and the receivers more likely to click on a phishing email.
Phishing Emails Bypassing Security Defenses at Record Rate
All these new propagation and obfuscation methods utilized by cybercriminals mean that, while the overall phishing volume hasn’t increased, the number of phishing emails that bypass security defenses is rising.
For instance, emails that evaded Microsoft defenses have increased by 25% in 2023 compared with 2022. Those that evaded secure email gateways (SEGs) are up 29% over the same period.
In a public statement, Jack Chapman, Egress’s VP of Threat Intelligence, said that these findings should push email security defenders to change their anti-phishing approach.
“Legacy approaches to email security rely heavily on quarantine barring end users from seeing phishing emails, but as our report highlights, phishing emails will inevitably get through. This is one of the reasons why we’ve flipped the quarantine model on its head, adding dynamic banners to neutralize threats within the inbox. These banners are designed to clearly explain the risk in a way that’s easy to understand, timely, and relevant, acting as teachable moments that educate the user. Ultimately, teaching someone to catch a phish is a more sustainable approach for long-term resilience,” he commented.
The Most Popular Phishing Campaign Topics in 2023
Egress’s Phishing Threat Trends Report outlined the most popular topics used by phishing campaigns for every month of 2023 so far. These are:
- January: RingCentral impersonation
- February: Alias impersonation attackers tackers
- March: HMRC/IRS notification impersonation
- April: Security software impersonation
- May: Sextortion phish/life ruiners
- June: Lottery impersonation
- July: Salesforce/Meta ads
- August: Geek Squad
- September: Credit card payments
Read more: Booking.com Customers Targeted in Major Phishing Campaign
