A critical authentication vulnerability affecting the Appsmith low-code platform has been exploited to take over user accounts.
The issue, assigned CVE-2026-22794, allows attackers to manipulate password reset links by abusing a client-controlled HTTP header, ultimately leading to full account compromise.
The flaw occurs during Appsmith's password reset process. When a reset request is submitted, the platform uses the HTTP Origin header supplied by the client to build the password reset link sent by email. However, this header is not validated or restricted and an attacker can insert a malicious value and redirect sensitive reset tokens to infrastructure under their control.
An attacker can request a password reset for a victim's email address while modifying the Origin header to point to an attacker-controlled domain. The victim receives a legitimate email from Appsmith, but the embedded reset link directs them to the attacker's server instead of the real application.
Once the link is clicked, the reset token is exposed. The attacker can then use that token to set a new password on the genuine Appsmith instance and gain access to the victim's account. The vulnerable endpoint always returns a successful response, which helps conceal abuse and enables repeated attacks without raising alerts.
Impact and Mitigation
Appsmith is widely used to build internal tools such as dashboards, admin panels and data-driven business applications.
These deployments often connect to sensitive databases, APIs and internal systems, making authentication flaws especially serious.
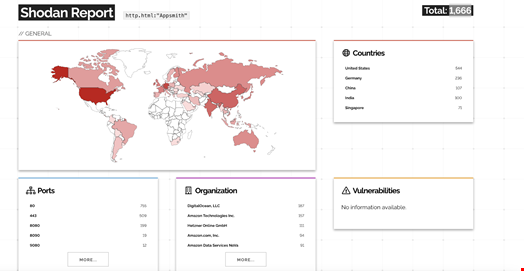
According to internet scanning data referenced by Resecurity, 1666 Appsmith instances are publicly accessible.
A significant portion appear to be running version 1.x, including releases up to 1.92, all of which are affected by CVE-2026-22794. Appsmith 2.x versions are not vulnerable.
Key details highlighted in the findings include:
-
Affected endpoint: /api/v1/users/forgotPassword
-
Impacted versions: Appsmith 1.92 and earlier
-
Fixed release: Appsmith 1.93
Exploitation of the flaw can lead to full account takeover, including administrator access. From there, attackers could manage users, alter applications or access connected business data.
The attack also carries phishing and trust-abuse risks because the malicious links are delivered through legitimate Appsmith emails.
The issue was resolved in Appsmith version 1.93 through stricter validation of the Origin header and enforcement of a trusted base URL.
Infosecurity contacted Appsmith for comment on the flaw, but has not received a response at the time of writing.
