A new strain of yet another ransomware campaign has been discovered in which the malicious actors have expanded payment options beyond Bitcoin; they are instead offering alternatives (such as PayPal) that include a phishing link, according to MalwareHunterTeam.
Attackers are stealing a page from Daedalus and are killing two birds with one stone by including a link to make a payment. To obtain the decryption key, victims can follow the link to the PayPal phishing page, where their login credentials are stolen. The combination of two threat vectors makes this attack particularly dangerous for unsuspecting victims.
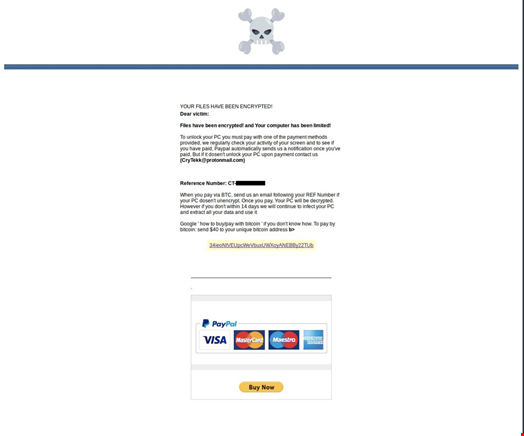
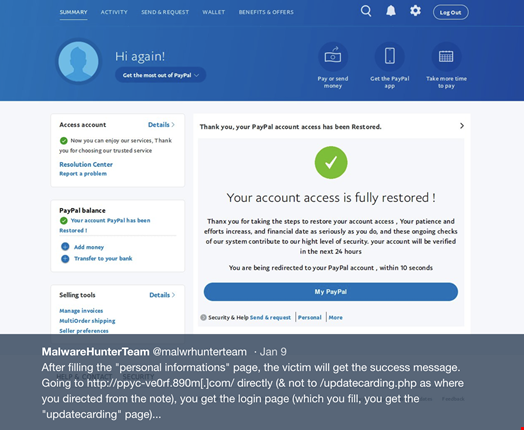
The new attack method combines “a ransom note that direct victims to a PayPal phishing page...Clicking on the Buy Now button, it directs to the credit card part of the phish already (so the login part is skipped). After filling & clicking Agree comes the personal info part & then finished,” the team tweeted. Once that payment is processed, the victim receives a confirmation.
For victims who pay with Bitcoin, the threat actors also requested that victims send an email with a reference number, which is provided in the ransom.
“Malicious actors are continually becoming more sophisticated. With this particular campaign involving phishing as an immediate follow-up threat vector to the ransomware, this attack has the potential to cause significant harm,” said DomainTools’ senior security adviser, Corin Imai.
“Not only will victims be dealing with the impact of ransomware, but many will also be directed to a carefully crafted phishing site that will attempt to steal their credentials. As seen in past attacks, ransomware campaigns have targeted individuals with the threat of releasing compromising content or rendering their computers useless, leaving victims feeling that they have no choice but to pay up. The best advice in this scenario is to be hyper-vigilant, double-check URLs, and when in doubt, don’t click.”
