One of the most prolific North Korean-linked cyber threat groups, Labyrinth Chollima, has recently evolved to make to three distinct hacking groups, according to CrowdStrike.
In a new blog published on January 29, the cybersecurity giant said the three groups will now be tracked as Labyrinth Chollima, Golden Chollima and Pressure Chollima.
The firm assessed “with high confidence” that while Labyrinth Chollima continues to focus on cyber espionage, targeting industrial, logistics and defense companies, the other groups have shifted towards targeting cryptocurrency entities.
Each group is using distinct toolsets in their malware campaigns, according to CrowdStrike. The toolsets are all evolutions of the same malware framework used by Labyrinth Chollima in the 2000s and 2010s.
However, the CrowdStrike threat intelligence analysts said that despite now operating independently, these three adversaries still share tools and infrastructure, indicating centralized coordination and resource allocation within the North Korean cyber ecosystem.
Labyrinth Chollima, One of Many Lazarus Aliases
Labyrinth Chollima (also known as UNC4034 and Temp.Hermit) is one of the most active cyber threat groups attributed to North Korea.
According to CrowdStrike, the group is responsible for some of North Korea’s most notable intrusions, including destructive attacks against South Korean and US entities and the global WannaCry ransomware incident.
While some of the group’s past operations have been attributed to the Lazarus Group, it now seems that most cyber threat intelligence analysts have abandoned this latter name as it encompasses too many distinct teams within North Korean attributed hacking ecosystem.
For example, the entry for the Lazarus Group on Malpedia, a cyber threat intelligence repository maintained by Germany’s Fraunhofer research institute, lists 42 different aliases, highlighting how broadly the name has been applied to distinct North Korean hacking teams.
Labyrinth Chollima’s Beginnings and Stardust Chollima Emergence
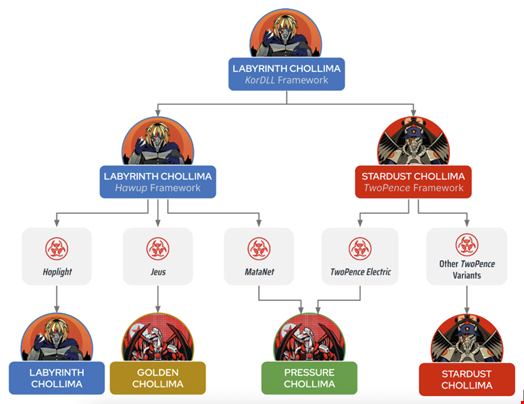
CrowdStrike started tracking the Labyrinth Chollima group as a distinct cyber hacking group tied to the North Korean regime when it discovered the KorDLL malware framework used in the wild between 2009 and 2015.
KorDLL is a source code repository containing implant templates, command-and-control (C2) protocols, libraries for common tasks and code for various obfuscation techniques.
This framework “spawned several epoch-defining malware families, including Dozer, Brambul, Joanap, KorDLL Bot and Koredos,” said CrowdStrike.
It later evolved into the Hawup and TwoPence malware frameworks, which led CrowdStrike to split Labyrinth Chollima into two groups: Labyrinth Chollima, which used the Hawup framework and Stardust Chollima, which used the TwoPence framework and its evolved versions.
Labyrinth Chollima, Golden Chollima and Pressure Chollima
Today, CrowdStrike is sharing a new evolution of the Hawup framework into three distinct versions. These include the Hoplight framework used by Labyrinth Chollima, the Jeus framework used by Golden Chollima and the MataNet framework used by Pressure Chollima alongside the TwoPence framework.
Aside from using distinctive tooling, the three groups also differ in their targeting and techniques, tactics and procedures (TTPs):
- Golden Chollima focuses on consistent, smaller-scale cryptocurrency thefts in fintech-heavy regions using cloud-focused tradecraft and recruitment fraud lures
- Pressure Chollima pursues high-value, opportunistic crypto heists globally with advanced, low-prevalence implants
- Labyrinth Chollima conducts espionage against defense, manufacturing and critical infrastructure sectors via zero-days, employment-themed lures, and kernel-level malware
