A hyper-active LockBit group led to a surge in ransomware campaigns in the last quarter of 2023, according to XDR security provider ReliaQuest.
In its Q4 2023 Ransomware Trends report, ReliaQuest found that ransomware activity was up 80% between October and December 2023 compared with the same period in 2022.
Over this period, a total of 1262 victims were listed on data leak sites, with victims ranging from several industries, including manufacturing, construction, professional, scientific and technical services.
LockBit Dominates the Threat Landscape
LockBit was the most active threat group, with 275 victims listed on data leak sites over the studied period.
This is more than twice as many victims claimed than the second most active group, Play, which claimed 110 victims on data leak sites in Q4 2023. ALPHV/BlackCat came third with 102 victims claimed, NoEscape came fourth (76), and 8Base came fifth (75).
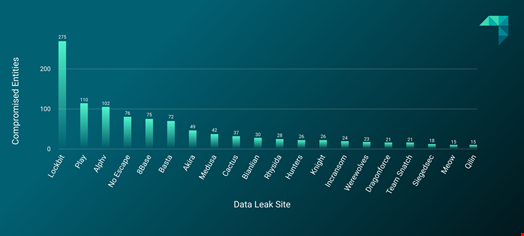
This domination aligned with previous trends since LockBit was the most active group throughout 2023.
ReliaQuest observed that LockBitSupp, the group’s public representative, had been consistently trying to recruit members of NoEscape and ALPHV, whose activity has been disrupted by law enforcement operations.
Read more: Law Enforcement Confirms BlackCat Take Down, Decryption Key Offered to Victims
For instance, LockBitSupp had been observed offering the use of LockBit’s data-leak site and negotiation panel to both groups’ affiliates.
“It’s unclear whether the recruitment scheme worked, but at least one organization whose compromise was linked to ALPHV ended up being named on LockBit’s leak site,” the ReliaQuest report noted.
Meanwhile, the NoEscape and Play ransomware groups seemed to have increased their activity during the last quarter of 2023.
Citrix Bleed Up, MOVEit Down
November saw an uptick in ransomware victim claims, with 484 for that month only.
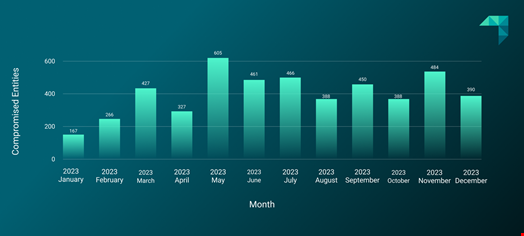
ReliaQuest attributed this spike to increased exploitation of the Citrix Bleed vulnerability, which was primarily exploited by LockBit affiliates.
“On top of that, November brought new aggressive extortion tactics by the ransomware group ALPHV, involving the US Securities and Exchange Commission (SEC) to pressure their targets,” the report reads.
However, the MOVEit campaign seemed to have cooled down, with the Clop group naming 95.3% fewer victims in Q4 2023 than in the previous quarter.
Read more: MOVEit Exploitation Fallout Drives Record Ransomware Attacks
2024 Ransomware Groups’ Tactics Predictions
Based on its data, ReliaQuest expects that the rise in ransomware claims will continue in 2024.
The firm also shared 2024 predictions regarding the tactics of some of the most active ransomware groups.
These include:
- LockBit’s NetScaler Affinity: LockBit has been exploiting vulnerabilities in NetScaler, a widely used networking technology, to target high-value organizations (banks, governments, law firms, etc). Given the profitability and success of these attacks, ReliaQuest assesses that LockBit will probably continue its NetScaler exploitation and industry focus.
- Clop’s Comeback Potential: Although Clop’s activity reduced towards the end of 2023, ReliaQuest expects the group to “make a comeback” in 2024. “This tapering after an activity surge has been seen with Clop before, following a 2020–21 campaign that abused several zero-days,” the report reads.
- NoEscape’s Silent Threat (for Now): Although NoEscape seems to have disappeared, having taken down its data leak site, for instance, ReliaQuest said it would likely resume its activity at some point in the future, albeit probably under another name. This assessment is “based on the fact that NoEscape emerged as a rebrand of ‘Avaddon,’ and given its success with multi-extortion tactics.”
