Researchers at Trend Micro discovered spyware that had successfully disguised itself as a legitimate Android application. Initially found in a game called Flappy Birr Dog, the malware has been widely distributed, affecting users from 196 different countries.
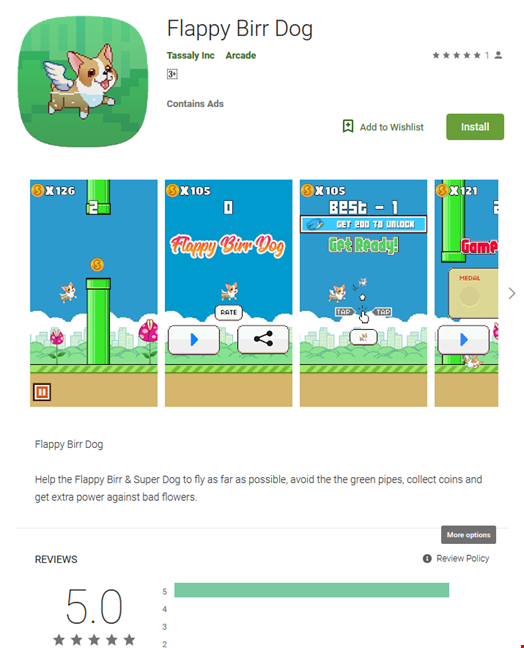
According to research, the application was available on Google Play and had more than 100,000 recorded downloads from users worldwide. In total, the spyware was discovered in six different applications, all of which have been suspended from Google Play, though five of the apps were removed in February 2018.
The spyware, ANDROIDOS_MOBSTSPY, was reportedly stealing information that included not only user location but also SMS conversations and call logs. “It uses Firebase Cloud Messaging to send information to its server. Once the malicious application is launched, the malware will first check the device’s network availability. It then reads and parses an XML configure file from its C&C server,” researchers wrote.
In addition, the malware has phishing capabilities and displayed fake pop-ups from Facebook and Google. The pop-ups prompted the user to enter log-in information, though the attempt would fail and deliver an "unsuccessful log-in" alert, albeit too late because the credentials had already been stolen.
“Attackers are getting better and better at sneaking malware onto official app stores, which they view as the ultimate distribution channel for their criminal schemes," said Sam Bakken, senior product marketing manager, OneSpan. "And we won’t see this trend abate any time soon with the potential for fraud that opens up via mobile apps and devices. Not only do we all need to continue to educate users on mobile hygiene, banks, retailers, etc., that engage with their customers via mobile apps need to be sure their apps are secured against malware that targets their apps and users. Thankfully, technology exists that can be easily integrated into existing mobile apps that monitors those apps in real-time to take action on attacks such as these.”
