A new phishing campaign targeting major financial and technology firms has been uncovered by cybersecurity researchers.
SOCRadar dubbed the campaign Operation DoppelBrand and said it focused on Fortune 500 companies, including Wells Fargo and USAA, between December 2025 and January 2026, with infrastructure linked to earlier activity dating back to 2022.
The cybersecurity firm attributed the activity to a financially motivated threat actor known as GS7.
The campaign, described in a new report published on February 16, relies on lookalike domains and cloned login portals that closely imitate legitimate banking, insurance and technology websites.
Victims are lured through phishing emails and redirected to counterfeit pages where credentials are harvested and transmitted to Telegram bots controlled by the attacker.
In many cases, the operation goes further, deploying remote management and monitoring tools to gain persistent access to compromised systems.
Infrastructure Built for Scale
SOCRadar identified more than 150 domains tied to the latest wave of activity, with nearly 200 additional domains showing similar characteristics. The infrastructure is highly automated, using rotating registrars such as Namecheap and OwnRegistrar, Cloudflare hosting and short-lived SSL certificates issued within hours of domain registration.
Common traits include:
-
Recently registered domains with one-year terms
-
Automated SSL certificates from Let's Encrypt or Google Trust Services
-
Wildcard DNS records enabling rapid subdomain creation
-
Brand-specific subdomains mimicking banks, insurers and technology providers
The phishing pages replicate visual elements of legitimate sites, including logos, CSS styles and login form layouts. Some campaigns route victims through fake OneDrive interfaces before presenting spoofed banking portals.
Once credentials are submitted, data including IP address, geolocation and device details are forwarded to a Telegram group, allowing the attacker to filter and prioritise targets.
Remote Access and Monetization
Beyond credential theft, GS7 deploys legitimate remote access software such as LogMeIn Resolve to establish unattended access. Installers are delivered as MSI files, often accompanied by small VBS loaders that handle privilege escalation, silent installation and cleanup.
Researchers said the attacker appears to act as an initial access broker, selling or transferring compromised accounts to affiliates. In a direct exchange with SOCRadar, the individual claiming to be GS7 reportedly stated they had been operating for around ten years and provided screenshots of phishing panels bearing their handle.
Financially, blockchain analysis of a wallet shared during the investigation showed roughly 0.28 BTC received, equivalent to between $25,000 and $32,000 depending on market price at the time.
The primary targets include major US financial institutions, investment firms and insurance providers, alongside global technology and healthcare brands. English-speaking markets, particularly the US and Western Europe, account for the bulk of observed activity.
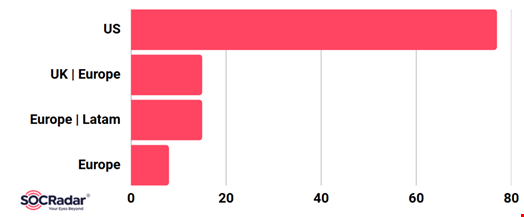
The SOCRadar report concluded that the combination of brand impersonation, automated infrastructure and legitimate remote management tools makes Operation DoppelBrand both scalable and difficult to disrupt.
