The Predator spyware, at the heart of the Predator Files affair in 2023, is still used in many countries, according to cybersecurity provider Recorded Future.
The spyware developer Cytrox and its umbrella organization Intellexa were associated with human rights violations by the Predator Files, a media project launched in September 2023 and coordinated by the European Investigative Collaborations.
However, in a new report published on March 1, 2024, Insikt Group, Recorded Future’s threat intelligence team, discovered new campaigns targeting mobile phones in several countries with the Predator spyware.
Specifically, the threat researchers identified evidence of the likely continued use of Predator within at least 11 countries: Angola, Armenia, Botswana, Egypt, Indonesia, Kazakhstan, Mongolia, Oman, the Philippines, Saudi Arabia, and Trinidad and Tobago.
This is the first time Predator use has been identified in Botswana and the Philippines.
No Need for Major Changes Within Predator Infrastructure
In the report, Recorded Future’s Insikt Group described a new multi-tiered Predator delivery infrastructure network consisting of delivery servers, upstream servers, and infrastructure.
The firm assessed that this new infrastructure is “highly likely associated with Predator customers,” suggesting that the spyware operators have not ceased selling their product following the Predator Files.
Instead, they’ve continued operating by implementing minimal changes to their mode of operation.
The new multi-tiered infrastructure network includes:
- Downstream delivery servers likely used for device exploitation and initial access. These host a domain spoofing feature targeted for particular entities that may be of interest to the target for social engineering purposes
- A consistent upstream virtual private server (VPS) IP address over Transmission Control Protocol (TCP) port 10514. These upstream servers are very likely used as hop points for anonymization purposes
- Static in-country internet service provider (ISP) IP addresses likely associated with Predator customers
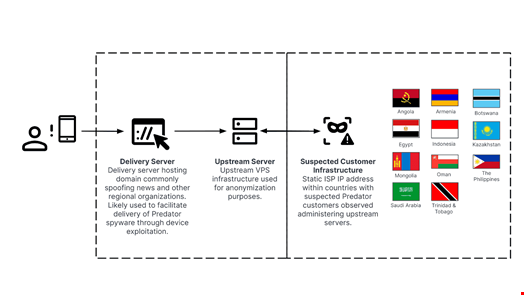
This infrastructure is largely similar to those identified in 2023 reports by Amnesty International, Citizen Lab and Sekoia.
Read more: Predator Spyware Linked to Madagascar's Government Ahead of Presidential Election
“While these patterns are relatively easy for threat researchers to identify, these techniques, tactics, and procedures (TTPs) are presumably producing satisfactory results, eliminating the need for changes,” Insikt Group researchers concluded.
“The proliferation and use of Predator and other spyware products, along with hack-for-hire services, outside of serious crime and counterterrorism law enforcement contexts will remain a substantial threat to various organizations and individuals.”
Evidence of New Predator Infrastructure Discovered
These findings are aligned with previous research published by French threat intelligence firm Sekoia on February 28, which recently observed a significant increase in the number of generic malicious domains associated with the Predator spyware.
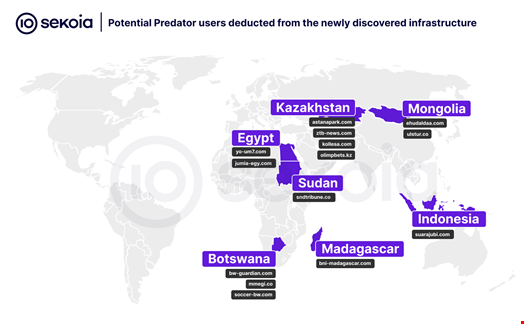
“We assess that some government services that use Intellexa surveillance solutions have taken notice of publications like ours and adapted their process to keep using the solution without giving hints about their targets,” Sekoia threat researchers wrote.
Sekoia was among the companies that signed the Pall Mall Process, an agreement initiated by the UK and France to tackle the proliferation and irresponsible use of commercial cyber intrusion capabilities, including spyware and hackers-for-hire services.
The agreement was signed by 25 countries and two regional institutions in London on February 6, 2024.
Read more: Governments and Tech Giants Unite Against Commercial Spyware
What is Predator Spyware?
Predator is a sophisticated mercenary spyware designed for use on both Android and iPhone devices. It has been active since 2019 and was developed by Cytrox, now part of Intellexa.
Predator can be installed with either ‘one-click’ or ‘zero-click’ attacks and leaves minimal traces on the mobile phones it has been installed on.
Once downloaded, Predator gains unfettered access to a device's microphone, camera and all stored or transmitted data, including contacts, messages, photos, and videos – all without the user's knowledge.
Its design incorporates Python-based modules, facilitating the introduction of new functionalities without the need for repeated exploitation.
Between 2021 and 2023, diverse instances of attempted and successful Predator infections have been documented, affecting individuals across various sectors and countries. Notable examples include:
- December 2021: Citizen Lab reported on two Egyptians, the exiled politician Ayman Nour and an anonymous host of a popular news program, who had been successfully infected with Predator after clicking on links sent via WhatsApp.
- April 2022: Inside Story reported that Thanasis Koukakis, a journalist at News and contributor to various news outlets such as CNN, had been successfully infected with Predator.
- July 2022: Documento revealed that Nikos Androulakis, the leader of an opposition party in Greece and a sitting Member of the European Parliament, had been unsuccessfully targeted by Predator in 2021 and wiretapped by the Greek National Intelligence Service (NIS).
- March 2023: Artemis Seaford, a Meta executive with dual US-Greek citizenship, was reportedly targeted with Predator and allegedly wiretapped by the NIS.
- September 2023: Citizen Lab revealed that Ahmed Eltantawy, a former Egyptian Member of Parliament, had been targeted multiple times with Predator between 2021 and 2023.
- October 2023: Amnesty International revealed a surveillance operation by a Predator customer linked to Vietnam targeting at least 50 social media accounts belonging to 27 individuals and 23 institutions between February and June 2023.
