The Russian-backed hacking group Sandworm deployed data wiper malware in Ukraine in the second and third quarter of 2025, according to ESET.
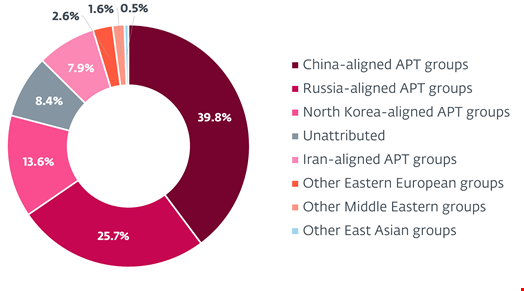
In its APT Activity Report Q2 2025–Q3 2025, the Slovakia-based cybersecurity company provided an overview of the activity of advanced persistent threat (APT) groups across the world from April to September 2025.
The report, published on November 6, revealed that Sandworm deployed data wipers, including Zerolot and Sting against organizations in Ukraine.
Targets ranged from governmental entities, companies in the energy and logistics industries and the grain sector.
Sandworm, also known as APT44, Telebots, Voodoo Bear, Iridium, Seashell Blizzard and Iron Viking, has been associated to Russia's military intelligence service’s (GRU) unit MUN 74455 by several cybersecurity companies and government agencies.
ESET assessed that the group’s likely objective for deploying new wipers was to weaken the Ukrainian economy.
Russian Groups Use Spear Phishing and Backdoor For Cyber Espionage
The ESET report noted that other Russian-aligned APT groups also maintained their focus on Ukraine and countries with strategic ties to Ukraine, while also expanding their operations to European entities.
While Sandworm’s objective seemed to be to disrupt Ukrainian organizations, other Russian nation-state groups pursued cyber espionage goals through a combination of spear phishing campaigns and backdoor implants.
Gamaredon remained the most active APT group targeting Ukraine, with a noticeable increase in intensity and frequency of its operations during the reported period.
“This surge in activity coincided with a rare instance of cooperation between Russia-aligned APT groups, as Gamaredon selectively deployed one of Turla’s backdoors. Gamaredon’s toolset, possibly also spurred by the collaboration, continued to evolve, for example, through the incorporation of new file stealers or tunneling services,” the ESET researchers wrote.
Notably, ESET reported that another Russia-aligned threat actor, InedibleOchotense, conducted a spear phishing campaign impersonating the cybersecurity company.
“This campaign involved emails and Signal messages delivering a trojanized ESET installer that leads to the download of a legitimate ESET product along with the Kalambur backdoor,” the report read.
Some Russian groups expanded their targeting beyond Ukraine.
For instance, RomCom, another of the most active Russian APT groups, exploited a zero-day vulnerability in WinRAR to deploy malicious DLLs and deliver a variety of backdoors, with a focus on the financial, manufacturing, defense and logistics sectors in the EU and Canada.
Overview of Global APT Activity
The ESET report also highlighted China-aligned APTs continued focus on geopolitical espionage, targeting Latin America (FamousSparrow), Southeast Asia, the Us US and Europe (Mustang Panda), Taiwan’s healthcare (Flax Typhoon) and Central Asia’s energy sector (Speccom).
Meanwhile, Iran-aligned hacking group MuddyWater escalated its internal spear phishing tactics – sending malicious targeted emails from compromised inboxes within the target organization – while BladedFeline updated infrastructure and GalaxyGato deployed an upgraded backdoor and DLL-hijacking credential theft.
Finally, some North Korea-aligned APTs expanded their cryptocurrency heists and espionage tactics to Uzbekistan, while several groups from the same country – DeceptiveDevelopment, Lazarus, Kimsuky and Konni – were observed targeting South Korean diplomats and academics for revenue and geopolitical gains.