Top UK universities have had their services impacted by a DDoS attack, which has been claimed by the Anonymous Sudan hacktivist group.
The University of Cambridge’s Clinical School Computing Service revealed the incident in a post on its X (formerly Twitter) account on February 19, stating that internet access will be intermittent.
It said that the attack started at 15.00 GMT on February 19, with “multiple universities” impacted.
In an update on the morning of February 20, the service said that disruption to the network appears largely over, although some systems remain impacted.
Varsity, the independent newspaper for the University of Cambridge, reported that the attack had affected access to student IT services such as CamSIS and Moodle.
The attackers targeted the Janet Network, a high-speed data-sharing network used by researchers, according to the Varsity report. This service is used by a number of UK universities.
The Janet network is managed by Jisc, a UK not-for-profit provider of network and IT services to the higher education sector.
The University of Manchester also reported connectivity issues as a result of the DDoS attack, stating on its X account on February 19 that the availability of IT services off campus were impacted.
Cyber incident: Ongoing network connectivity issues
— The University of Manchester (@OfficialUoM) February 19, 2024
Earlier today (Monday 19 February), IT Services were made aware of network connectivity problems impacting several Universities, including our own.
We have now been made aware that the issues have been caused by a cyber…
In a follow-up post on February 20, the institution said the network connectivity issues have stabilized, with IT services now available on and off campus.
“However, you may continue to notice performance issues during stabilisation,” the University noted.
It added that it is continuing to monitor the situation and resolve any outstanding issues with partners, including Jisc.
Anonymous Sudan Claims Responsibility for University DDoS Attacks
Hacktivist group Anonymous Sudan claimed responsibility for the attack on the universities.
Hacktivist tracker X account CyberKnow shared a screenshot of a post by the gang, in which they cited the UK government’s support for Israel’s military action in Gaza and the bombing of the Houthi movement in Yemen as the reason for the attack.
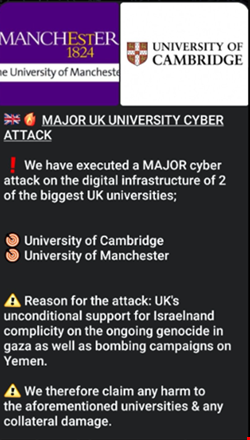
Anonymous Sudan has frequently been linked to politically motivated DDoS attacks. It claimed to have launched numerous cyber-attacks against the Israeli government and media organizations in the wake of Hamas’ assault on Israel on October 7, 2023, which started the conflict in Gaza.
UK Institutions Targeted by Hackers
Renowned UK institutions appear to be a growing target for cyber-threat actors.
The British Library is still in the process of recovering its digital services as a result of a ransomware attack in October 2023.
Gerasim Hovhannisyan, CEO and co-founder of EasyDMARC, noted that the University of Cambridge’s Library itself is in the process of restoring systems following the British Library attack.
He said that well-known institutions like universities must be particularly vigilant at this time.
“While DDoS attacks themselves usually don’t result in data loss, they can be used to mask the real malicious intentions of cybercriminals.
“With AI lowering the bar of who can develop and carry out cyber-attacks and the ransomware-as-a-service industry further expanding that demographic to anyone with sufficient funds, universities must look at the state of their cybersecurity postures seriously,” he commented.
Research published by KnowBe4 on February 19 found an “exponential” increase in cyber-attacks against UK higher education institutions. The report cited research showing that only half of higher education institutions have a cybersecurity strategy.
Keiron Holyome, VP UKI & Emerging Markets, BlackBerry Cybersecurity, noted that universities are seen as a soft target by threat actors. This has been exacerbated by the expanded threat environment following the shift to remote learning, connected learning technologies and more connections to often-unsecured devices owned by the students.
“IT support is often limited, budgets tight, and many use standard software provided to the education sector. If a vulnerability is found in that software, it won’t take long for the criminals to find it and exploit it,” explained Holyome.
