The first part of our series supplied an insight into the overall questions and possibilities than Security Operation Centre (SOC) architecture can offer. While an architectural deployment can provide efficiency and utilization across the spectrum of the working day, its implementation must have a workforce at its helm.
As a SOC becomes progressively more complex, the workforce structure adapts from a hierarchical structure, incorporating automation, to a fluid and dynamic workforce that lends from many disciplines within IT, Science and Mathematics.
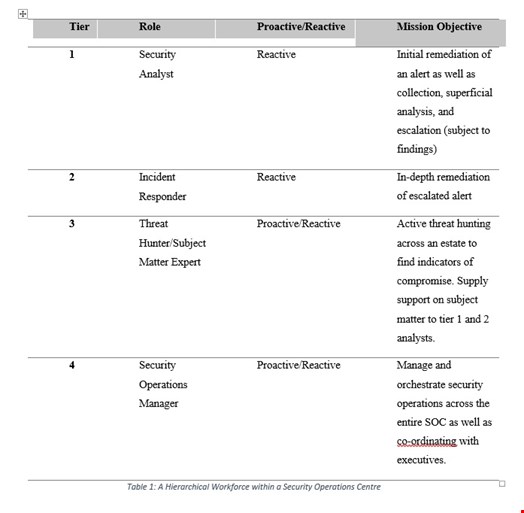
A workforce with an intelligent makeup across a range of skillsets and experience can be the difference between an incident or prevention. It is common to view a Security Operations Centre in a hierarchical structure that focuses on security analysts as tier one, incident responders as tier two, subject matter experts as tier three, and management as tier as four, which is similar to that of other fields e.g., Engineering and Software Development.
While the roles are distinct, clear objectives are defined, and a state of reaction can be associated with an immature SOC as seen in Table 1.
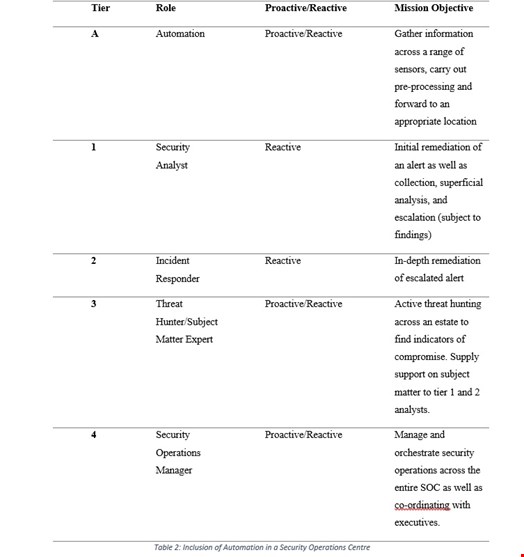
However, with the growing complexity and breadth of security monitoring that a SOC must endeavor, the rigidness of a hierarchical workforce, is demonstrated as a drawback. The progressive implementation of automation can provided an increase in utility and efficiency in gathering, analyzing, and reporting on incidents within a SOC capability. This has been seen through the integration of automation as a fundamental tier (referred to as tier A) within a SOC workforce model as seen in Table 2.
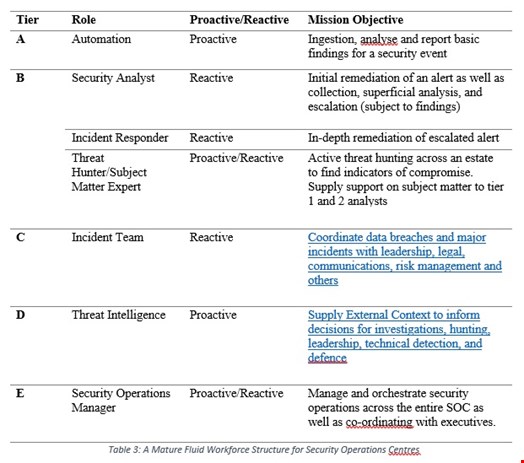
As a SOC becomes dynamic and further complex, the overall workforce hierarchy disseminates into a fluid agile structure allowing for adaptability, knowledge transfer, and speed. Table 3 illustrates a close relationship between skillsets of analysts during an incident, instead of an escalation culture.
The implementation of this structure could improve new analysts through the internal training mechanism of shadowing and reverse shadowing, as seen within the field of medicine and IT. With the inclusion and fluidity of multiple members of the team the overall benefit of visibility and a possibility in reducing stress through a wider network and experience pool could be a method in which organizations challenge such issues as lack of visibility, burnout, and training.
While the job roles and structures are changing with the shift in complexity within a SOC, many other auxiliary roles should also be noted in the success of any SOC, such as:
- Consultants,
- Administrators,
- Human Resources,
- Governance, Risk and Compliance
While these only present a partial view of a SOC’s auxiliary personnel, they provide a well-rounded improvement to the technical, sociological, law, and overall financial structure of a well-run SOC.
However, while the field of cybersecurity has seen the rise in SOC capabilities, the deficit in a skilled labor pool can lead more organizations to look at managed Security as a Service providers as a method in which remediates many of the overall issues that they may face during the expansion of the organizations’ SOC capability as highlighted in Part 1.
As many organizations are beginning to develop complexity in their security posture, many of the non-technical structures must be adapted to meet future demands. This can be seen through the changing in the overall organizational structure through the workforce.
While automation has provided a capability in which helps aid the workforce in differentiating between useful and useless information, further measures are required to be implemented to help mitigate the overall stress impact and high turnover that has been seen within the field of security operations.
Jack Whitter-Jones is a security enthusiast that is studying for a PhD within the field of Security Operations. Two prime focuses are on detecting sophisticated attacks through the ingestion and analysis of data via the utilization of automation and machine learning, as well as the creation of toolkits that evade traditional intrusion detection systems. Outside of his PhD, Jack lectures PHP both at masters level as well as second year degree students.