The market for cybercrime has become one in which many individuals and organizations fear. With a global reach, the internet has provided the platform for adversaries that have different agendas for cybercrime.
The value of user data has become a principal component of an organizations’ revenue stream. This can be seen through the total earnings of ad-revenue generated per year against the total earnings of Facebook, Amazon and Google, of which are global leaders within the technology industry.
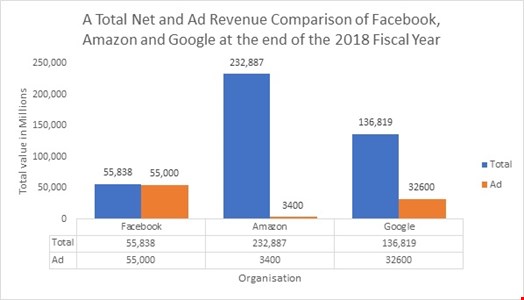
With the value of data being key to the success of an organization, the reliance on a Security Operations Centre (SOC) as their overall means of defensive capability is paramount. However, with the importance of securing data, the technical landscape that organizations employ is extremely vast encompassing web servers, email servers, file servers, cloud backups and Internet of Things devices, which all hold different jurisdictions, compliance requirements and hardening methods.
Many organizations are beginning to discover the importance of a SOC in aiding their defensive capability. Small, medium, and larger organizations ranging in different sectors such government, technology, cybersecurity, finance, and banking are increasingly seeking value from internal implementations, Managed Security Service Providers (MSSP), managed detection and response (MDR), or cloud-based models to achieve their overall needs.
While there is a difference of implementation, all providers of SOC capability work typically towards a 24/7 monitoring capability, encompassing four distinct areas:
- Workforce
- Organizational Aspects
- Technological Capability
- Operational Techniques
With the global reach of many organizations, the overall architectural implementation should be considered before further investment. Internal deployment vs the external deployment provides strengths and weaknesses:
Internal
Advantages
- Dedicated Staff
- Log stored Locally
- Most likely to notice correlations between internal groups
- Potential to be most efficient
- Solutions are generally easier to customize
- Knows environment better than third-party
Disadvantages
- Larger Up-Front investment
- High Pressure to show return-on-investment
- High potential for collusion between analyst and attacker
- Can be hard to find competent SOC Analysts
- Less likely to recognize large scale, subtle patterns that include multiple groups
External
Advantages
- Avoid capital expenses
- Exposures to multiple customers in similar industry segment
- Often cheaper than in-house
- Less potential for collusion between monitoring team and attacker
- Good security people are difficult to find
- Unbiased
- Potential to scalable and flexible
- Expertise in monitoring and SIEM tools
- SLA
Disadvantages
- Contractors will never know your environment compared to internal employees
- Sending jobs outside and organization can lower morale
- Lack of dedicate staff to a single client
- Lack of capital retention
- Risk of external data mishandling
- Log data not always achieved
- Log data stored off-premises
While the architecture can vary, the developing technological landscape orientates around automation, orchestration, ingestion, analysis, reporting and disseminating of threat intelligence. Such technologies that are typically seen within a SOC include:
- Security Incident and Event Management Systems (SIEM) - Splunk, Elasticsearch, Arcsight, and LogRhythm
- Security Orchestration, Automation and Response (SOAR) - Tines.io, FireEye Security Orchestrator Demisto and DFlabs Incman
- Incident and Threat Hunting Platforms - SecurityOnion, RockNSM and HELK (Hunting ElasticStack)
- Network Intrusion and Prevention Systems - Zeek, Snort, Suricata, Corelight and Dark Trace
- Host Intrusion and Prevention Systems - OSQuery, Crowdstrike, Wazuh, Carbon Black and Sophos Cloud Intercept X
While the breadth of technologies can be broad, and the architectural implementations diverse, a central point of access through an on-premises SIEM or via a cloud, where sensory information from sources like that of host-based and network-based intrusion detection are ingested, will always be within any landscape that implements a form of security architecture.
The implementation and cost of a SOC that can cover the overall landscape of an organization can be considerable, especially where the financial investment of internal SOC capability is heavily distributed across recruitment of operational analysts, management systems and process development. However, an external SOC can take the burden of the security posture without such large financial overheads. This can be achieved through the investment of Cloud-based security or MSSP/MDR solutions.
Based on the research that has been conducted, the implementation of SOC capability can be aligned through the initial investment of acquiring a cloud-based implementation or MSSP/MDR to begin with, with a strategy to bring it in-house in the future. This advice comes in two ways: cloud/MSSP/MDR has provided a means for the scalability, agility and on-demand access that can be scaled towards customers that have similar business models as other customers, while the future development of in-house architectures will always encompass cloud-based technologies to keep up with the growing demand of any business.
With the backing of large organizations, the continued development into platform features such as Microsoft Azure Sentinel and AWS Guard Duty will provide a support component to the overall platform. With the added bonus of a reduced overhead in managing technologies and recruitment costs, and having a plethora of documentation and a workforce that have well-defined methodologies to implement data collection, analysis and reporting for any future business development.
A further recommendation, is the NCSC UK Government Security Operations Centre buyers guide which is tailored towards answering key questions when organizations are looking to establishing their own in-house SOC or purchasing a third-party capability through a cloud, MSSP or MDR provider.
Jack Whitter-Jones is a security enthusiast that is studying for a PhD within the field of Security Operations. Two prime focuses are on detecting sophisticated attacks through the ingestion and analysis of data via the utilization of automation and machine learning, as well as the creation of toolkits that evade traditional intrusion detection systems. Outside of his PhD, Jack lectures PHP both at masters level as well as second year degree students.