Managing application risk has a lot to do with managing data. To mitigate application risks, it’s necessary to gather data from heterogeneous and sometimes far-flung sources—data about assets, vulnerabilities, business impact, users, threat intelligence, remediation workflows and more. Without a coherent data ontology, application security will bog down and become both inefficient and deficient.
CISOs have options when it comes to mitigating application risk. One approach is to do nothing and remediate vulnerabilities in applications only after they make the news for their role in a disclosed breach. This is not a wise approach, but it is the reality for many resource-constrained organizations.
A better practice is to manage application risks proactively, either as part of a broader cyber risk management program or as a standalone vulnerability management initiative focused on software infrastructure. It is then possible to accurately identify and triage application risks and intelligently prioritize mitigation or remediation efforts towards the most critical ones.
Application Risk Management functions can be grouped into distinct stages:
- Risk assessment and vulnerability identification
- Risk analysis and prioritization
- Risk remediation and mitigation
These processes must be continuously supported by analytics to effectively engage and inform all relevant stakeholders. A continuous evaluation and feedback loop must be established to ensure the program constantly evolves to focus on the most urgent and impactful factors.
Risk assessment and vulnerability reporting presents the first significant data management challenge faced by appsec programs. Application risks are widespread and occur in many contexts. To effectively assess the complete scope of software infrastructure, organizations must leverage a variety of assessment and monitoring tools which are often developed by different security vendors and follow their own methodology and nomenclature. They are also often owned by different teams depending on the nature of assessment being conducted, creating further silos of information.
Application infrastructure itself is never static. It is constantly evolving with software being upgraded and integrated with an ever-changing collection of systems, some of which may belong to other business entities.
For example, consider what happens when you integrate your website with an Enterprise Resource Planning (ERP) system. In doing so, you may inadvertently expose your ERP data to breach by means of a SQL injection attack. There are so many dependencies and moving parts, it can be difficult to determine the seriousness (or indeed, the very existence) of the SQL injection risk exposure.
The data management challenge only becomes more daunting as we move to the analysis, prioritization and remediation stages. To accomplish these tasks effectively, we must go beyond the technical asset and vulnerability information being reported by assessment and monitoring tools.
We must integrate business context to better understand the potential impact of a risk; we must bring in threat intelligence to understand the likelihood that a vulnerability may be exploited by a malicious actor; and we must align risk remediation actions with existing ITSM systems and processes.
With every additional data source and integrated system, the need for mature data management and analytical processes increases drastically.
The application risk analysis process is data-intensive. In order to determine the seriousness of a risk, you have to incorporate as much context as possible. Common sources of application risk management data include:
- Vulnerabilities, e.g. Static Application Security Testing (SAST) findings, Dynamic or Web Application Security Testing (DAST) issues, Interactive Application Security Testing (IAST) issues, Software Composition Analysis (SCA) findings, pen test results, and so forth
- Asset Metadata, e.g. configuration management data, data classification, development stage, deployment status, technology stack
- Business Context, e.g. business impact, ownership and escalation chains, data classification, compliance requirements
- Threat Intelligence, e.g. exploit availability, zero-day, hacker chatter, exploit toolkits, malware activity
- Patch Intelligence, e.g. patch availability, patch coverage, remediation solutions, known fixes
- User access factors, e.g. privileged access, app administration
Assessing application risk requires clear delineation of the relationships between numerous and disparate risk data points surrounding the app. If there is a known malicious actor that exploiting this vulnerability to attack businesses, the analyst should factor that into the risk determination.
A comprehensive, coherent data ontology can ensure that all this relevant information is at the analyst’s fingertips when needed.
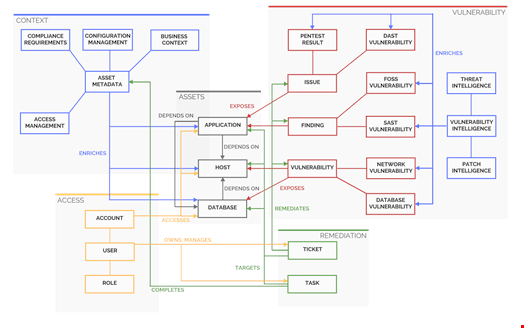
Example of application risk management data ontology displayed graphically in an application risk management tool
A cyber risk data ontology will map each application risk data point to all other relevant, connected pieces of information. Cyber Risk Management solutions provide the tools to make this happen. Enterprises can now understand where the threat of a vulnerability fits into the overall context of the application—including business context, user access considerations, threat intel and attempts at remediation.
A Cyber Risk Management solution makes it possible to collect, normalize, correlate and analyze application asset, vulnerability, context and threat data. It integrates the various relevant data sources into a single authoritative source of truth that can now be utilized by the different stakeholders involved in the Application Risk Management process. Data correlation and enrichment functions build the relationships between all the different data points in the ontology to highlight contexts necessary for informed decision-making.
Application risk management is an essential component of an effective cybersecurity program. Application risk mitigation has to be data- and context-driven or it will be inefficient and deficient. Achieving success requires tooling that can perform the demanding data management and analysis workloads inherent in the process. The right programs will build an accurate data ontology, prioritize vulnerabilities intelligently and track remediation continuously to deliver reliable, consistent improvements in security posture.
