A new malicious campaign is spreading malware against people in Iran, likely including non-governmental organizations and individuals involved in documenting recent human rights abuses during the protest wave in the country.
The campaign, discovered by the cyber threat research team at French cybersecurity firm HarfangLab, was first observed in early January 2026.
HarfangLab obtained malicious samples on January 23 and shared a malware analysis on January 29.
Dubbed RedKitten by the researchers, the campaign distributes forged ‘shock lures’ designed to target organizations or individuals seeking information about missing persons or political dissidents. These lures lead to a malware implant, dubbed SloppyMIO, that can collect and exfiltrate data, run arbitrary commands and deploy further malware with persistence via scheduled tasks.
The malware relies on GitHub and Google Drive for configuration and modular payload retrieval and uses Telegram for command and control.
The HarfangLab researchers assessed that it was built using AI tools, as indicated by multiple traces of large language model-assisted (LLM) development.
While the researchers could not reliably attribute the activity to an identified threat actor, they observed the use of techniques previously known to have been employed by Iranian state-sponsored attackers, alongside linguistic indicators.
They stated that they were confident the activity originated from a threat actor aligned with the Iranian government’s security interests.
Fake Forensic Files to Target Dissidents and Researchers
The RedKitten campaign begins with a password-protected 7z archive, titled "Tehran Forensic Medical Files" in Farsi, containing five malicious Excel spreadsheets. The files claim to list 200 individuals, allegedly protesters, who died in Tehran between December 2025 and January 2026, a period marked by unrest against the Iranian regime.
The Excel documents, named to appear as official records (e.g., "Final List_Victims_December 1404_Tehran_Part One.xlsm"), include five tabs of fabricated but disturbing data.
One sheet lists victims’ personal details alongside the security forces involved, such as the Islamic Revolutionary Guard Corps (IRGC), the Basij militia or the Ministry of Intelligence, while another provides graphic autopsy reports, including toxicology results. A third tab tracks body releases to family members and a final "Help" sheet urges users to enable macros, triggering the malware.
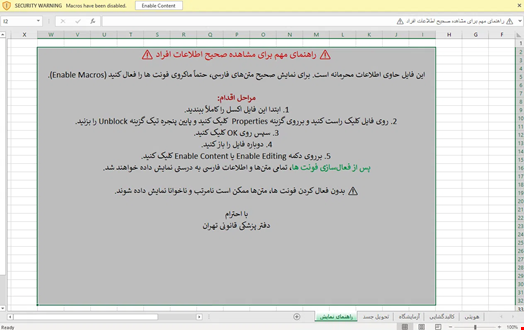
According to the HarfangLab researchers, the lures are designed to exploit emotional distress, targeting activists, journalists or families searching for missing loved ones.
However, the researchers noted that the data is riddled with inconsistencies, such as mismatched ages and birthdates and implausible workloads for the listed doctors, suggesting fabrication. The level of detail, including specific security agencies tied to each death, appears calculated to shock and provoke urgency – a tactic the researchers said is consistent with past Iranian cyber operations.
SloppyMIO Implant: Data Theft, Exfiltration and Spyware Capabilities
When opened, the malicious Excel file prompts the user to “Enable Content,” triggering a hidden VBA macro, a small program embedded in the document. This macro quietly extracts a more dangerous payload, a piece of malware written in C# that the HarfangLab researchers have dubbed SloppyMIO.
The name SloppyMIO hints at its messy design, as each infection generates slightly different code, making it harder for security tools to recognize and block.
Once activated, the malware uses clever tricks to avoid detection. It copies a legitimate Windows program (like AppVStreamingUX.exe) to a hidden folder, then forces it to load the malicious code as if it were a normal part of the system. To ensure it keeps running, the malware creates a scheduled task that launches itself every time the computer starts.
The hackers also left clues in the code suggesting it was at least partially generated by AI, with oddly named variables and comments that read like automated notes.
Unlike traditional malware that connects to suspicious servers, SloppyMIO uses Telegram to receive commands from its operators.
It first sends a "beacon" message to a hacker-controlled Telegram bot, announcing that the infected computer is online. The malware then periodically checks for new instructions, disguised as innocent chat messages.
To make detection even harder, the hackers hide their malware’s settings inside seemingly normal images (like memes or stock photos) using a technique called steganography, where data is concealed in the tiny, imperceptible details of a picture.
Once installed, SloppyMIO can perform a range of spying and sabotage tasks, including the following:
- Collect and exfiltrate files
- Run commands on the victim’s computer
- Download additional malware
- Install backdoors for long-term access
The hackers can send orders through Telegram, telling the malware to search for specific documents, execute programs or even spread to other machines.
Some versions of the malware also try to maintain persistence by creating scheduled tasks that reinstall it if removed.
RedKitten’s Victimology and Attribution
The malicious samples were uploaded by the HarfangLab researchers in the Netherlands to an online multiscanner. They said they cannot confirm if the uploader was an intended target or a researcher.
“We believe that non-governmental organizations and individuals involved in documenting recent human rights violations, as well as the horrendous level of violence demonstrated by the Iranian regime towards protesters, may be the intended targets of this campaign,” they wrote.
While the researchers did not clearly attribute this campaign at this stage, its infection chain shows overlaps with the tactics, techniques and procedures (TTPs) of the Iranian, IRGC-aligned threat actor Yellow Liderc (aka Imperial Kitten, TA456).
“Notably, this group has previously relied on malicious Excel documents to deliver .NET malware via ‘AppDomain Manager Injection’, specifically hijacking the same legitimate Windows binary, AppVStreamingUX.exe,” they wrote.
Additionally, the researchers outlined several clues in the RedKitten infrastructure that suggest the threat actor has links with previously observed Iran-aligned threat groups and speaks Farsi. For instance, the use of GitHub as a Dead Drop Resolver (DDR) and the use of Telegram for command-and-control (C2) have been reported in campaigns by separate Iranian threat clusters since 2022.
The researchers even noted the "tongue-in-cheek" use of kitten imagery in the payload, suggesting that the attackers may be playfully acknowledging the ‘Kitten’ naming convention commonly used by cybersecurity firms and government agencies to identify Iran-linked hacking groups.

“Distinguishing between Iranian-nexus actors is increasingly challenging due to the communalities shared between them and the growing adoption of LLMs in attack campaigns. This has been reported in groups such as Crimson Sandstorm and across the broader Iranian APT landscape,” the researchers concluded.
