The notorious cybercriminal forum Russian Anonymous Marketplace (RAMP) has reportedly been taken down by the FBI.
The news came on January 28, when several cyber threat intelligence (CTI) analysts noticed both RAMP clear and dark web sites were down and replaced by a law enforcement banner showing the message: “This site has been seized.”
The banner says the FBI seized the site in collaboration with the US Attorney’s Office for the Southern District of Florida and the US Justice Department’s (DoJ) Computer Crime and Intellectual Property Section (CCIPS).
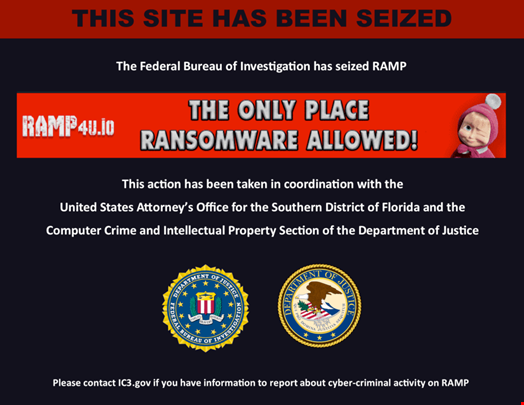
The notice also taunts the RAMP operators with a message saying, "The Only Place Ransomware Allowed!" and an image of Masha, a Russian cartoon character, winking.
While thew FBI has made no official statement at the time of writing, the domains linked to RAMP now redirect to seizure notices with FBI and DoJ seals and the nameservers have been updated to ns1.fbi.seized.gov and ns2.fbi.seized.gov, confirming the seizure by US law enforcement.
RAMP: The Dark Web Forum Where Ransomware Is Allowed
RAMP was created in 2012 as a site operating on the Tor network but rose to prominence in 2021, operated by people linked to the now defunct Babuk ransomware group. The RAMP forum in its current form was born after XSS and Exploit, the two main dark web forums in the Russian cybercrime landscape, as well as the English-speaking BreachForums, banned ransomware discussions.
The message on the FBI banner trolls RAMP’s position as the sole underground marketplace where talking about ransomware was allowed.
One of the individuals behind RAMP was Mikhail Matveev, a Russian national, also known under the aliases Orange, Wazawaka and BorisElcin. Matveev was arrested in Russia in 2024.
Another key operator, known as ‘Stallman,’ was still the forum’s administrator when the takedown occurred.
Rebecca Taylor, a threat intelligence researcher at Sophos, told Infosecurity that Stallman “played a central role in maintaining trust, enforcing rules and managing the platform’s technical operations.”
In a LinkedIn post shared after the takedown, Yelisey Bohuslavskiy, co-founder of intelligence firm Red Sense, explained that RAMP was created by individuals closely affiliated with the Russian security services as a response to the ransomware-as-a-service (RaaS) sprawl.
He said that until 2020, Russian, Belarusian and Ukrainian services had strong visibility into the traditional, highly organized cybercriminal groups like Ryuk, Conti, REvil, Maze, Ragnar, Netwalker and others.
“Part of that visibility came through control over Exploit and XSS via security-affiliated admins. Then RaaS exploded. The model sprawled uncontrollably: even forum admins had zero control over affiliates. That was the problem to which RAMP was the answer,” he added.
According to the CTI expert, RAMP was a prime hub for new and low-to-mid-tier ransomware groups to promote themselves, offer services and “be as visible as possible.”
“This worked. One of the first things a new group or actor did was post on RAMP - effectively identifying themselves to the authorities. It also improved visibility into non-Russian-speaking crews and attracted the usual ‘supply chain’ sellers: logs, loaders, initial access, exploits, etc,” Bohuslavskiy continued.
Tammy Harper, a senior threat intelligence researcher at Flare, described RAMP as “one of the most trusted ransomware-adjacent forums in the cybercrime ecosystem.”
She explained that the platform was “widely regarded as a high-trust escrow environment” and functioned as the main discussion hub for ransomware operators, intermediaries and affiliates.
Ben Clarke, a security operations center (SOC) manager at CybaVerse, explained that the reason for RAMP's success was that "it offered criminals with a marketplace supporting the entire attack chain, from the ability to buy stolen credentials, promote malware or sell and purchase ransomware services."
Many notorious ransomware groups, including LockBit, ALPHV/BlackCat, Conti, DragonForce, Qilin, Nova, Radiant and RansomHub, are understood to have operated on this forum at various points.
RAMP Administrator Confirms Takedown, No Plans to Rebuild
It has been reported that the individual known as Stallman issued an official comment regarding the RAMP seizure on January 28. The statement has circulated widely across underground discussion spaces.
Taylor told Infosecurity, “Following the seizure of RAMP, Stallman publicly stated on the XSS forum that the takedown had ‘destroyed years of my work’ and confirmed there were no plans to rebuild.”
“The post and takedown have driven significant chatter within underground communities, reflecting heightened concern, uncertainty and loss of confidence following the takedown,” she added.
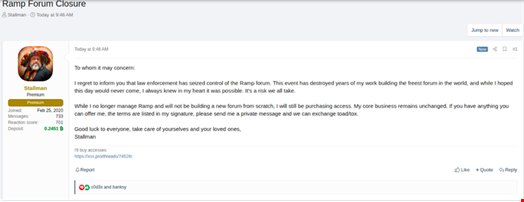
Sallman’s decision not to create a new version of RAMP is likely linked to concerns about his own freedom. Bohuslavskiy noted that the RAMP admin is now “a void asset for the Russian services” and is likely next on the list following a spate of arrests of cybercriminals in 2025.
Takedown Welcome, But Impact Limited
The RAMP takedown represents “a meaningful disruption to a core piece of criminal infrastructure,” commented Flare’s Harper.
Taylor told Infosecurity, “These operations not only disrupt and dismantle criminal infrastructure, but also sow mistrust, fear, and uncertainty among threat actors. The RAMP seizure is likely to provide valuable intelligence on criminal participants and create further opportunities for law enforcement action.”
Giomar Salazaar, a threat intelligence analyst at Outpost24, called the takedown “another major blow to the infrastructure supporting the digital extortion ecosystem," while Daniel Wilcock, a threat intelligence analyst at Talion, described it as a big win for law enforcement" and said it will provide "valuable information from the seizure around the threat actors using the services," such as their emails and IP addresses plus access to the financial transactions that took place on the market.
RedSense’s Bohuslavskiy welcomed any takedown of ransomware-enabling infrastructure. However, he painted a more nuanced picture of what it means for the future of cybercrime.
In his LinkedIn post, he mentioned four main likely consequences:
- The RAMP takedown will mostly impact low-tier actors as losing RAMP means losing market access and the ability to announce and ‘launch’ themselves
- It will also likely lead to major disruption to distribution and sales for underground sellers. However, Bohuslavskiy predicted that Telegram will absorb some of it
- It will have minimal impact on top-tier groups. This is because they understood RAMP’s affiliation to ransomware and largely stayed away from it
- Russian security services will lose some visibility into ransomware processes and sellers
Additionally, Talion's Wilcock also highlighted that while the RAMP operator claims to have no plans to rebuild another marketplace, other criminals are likely to turn to alternative underground markets to support their crimes. "This means that while RAMP has been taken down, which will create some inconveniences for its users, its impact on the overall cyber crime ecosystem will be limited.
Wilcock also noted that, "given that RAMP was heavily used by Russian criminals," it is "highly unlikely" the operation will lead to actual arrests.
