The US government has warned the healthcare sector that it is now the biggest target of the BlackCat ransomware group.
The joint advisory from the FBI, the Cybersecurity and Infrastructure Security Agency (CISA) and the Department of Health and Human Services (HHS), noted of the nearly 70 leaked victims of BlackCat since mid-December 2023, healthcare has been the most commonly victimized industry.
This follows a post by a BlackCat administrator encouraging affiliates to target hospitals in early December in response to law enforcement action taking down the Russian-speaking group’s leak site.
The group appeared to “unseize” its leak site shortly after the announcement.
BlackCat, also known as ALPHV, is reportedly behind the ongoing cyber incident affecting health tech firm Change Healthcare, which was first reported on February 21.
BlackCat Adapts Techniques Following Law Enforcement Operation
The advisory said that BlackCat actors are employing improvised communication methods by creating victim-specific emails to notify of the initial compromise.
For example, affiliates offer to provide unsolicited cyber remediation advice as an incentive for making a payment, such as “vulnerability reports” and “security recommendations” to prevent future attacks.
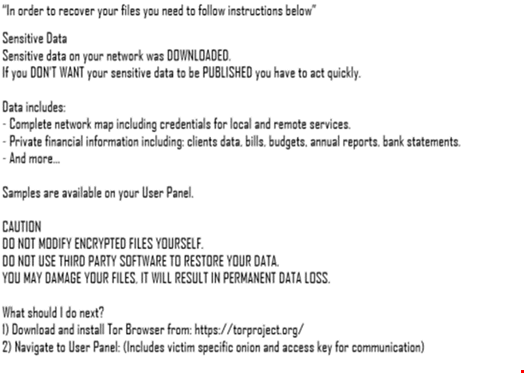
Additionally, in February 2023, the ransomware-as-a-service (RaaS) operator announced the ALPHV BlackCat Ransomware 2.0 Sphynx update, providing additional features for affiliates, including improved defense evasion.
This updated malware is capable of encrypting both Windows and Linux devices, and VMware instances.
Multifaceted Approach to Accessing Victim Networks
The agencies highlighted that many BlackCat affiliates employ advanced social engineering techniques to gain initial access, after undertaking open-source research on targets.
Threat actors frequently pose as company IT or helpdesk staff via phone calls or SMS messages to obtain credentials from employees.
After gaining access to the organization’s network, a sophisticated process takes place to gain access to the network and exfiltrate sensitive data.
Affiliates deploy remote access software such as AnyDesk, Mega sync, and Splashtop in preparation of data exfiltration, the advisory noted.
The attackers then create a user account, and gain domain access via Kerberos token generation. After gaining access, they use legitimate remote access and tunneling tools.
Tools like Cobalt Strike and Brute Ratel C4 provide “beacons” to command and control servers, while open-source adversary-in-the-middle (AitM) attack framework Evilginx2 enables them to obtain multifactor authentication (MFA) credentials, login credentials and session cookies.
While moving laterally through the network, affiliates employ allowlisted applications such as Metasploit to evade detection.
Mega.nz or Dropbox are used to move, exfiltrate, and/or download victim data, before finally the ransomware is deployed, with a ransom note embedded as a file.txt.
BlackCat affiliates communicate with victims via TOR, Tox, email, or encrypted applications.
Uniform resource locators (URLs) are sometimes used to live-chat with victims to convey demands and initiate processes to restore the victims’ encrypted files.
Some affiliates exfiltrate data after gaining access and extort victims without deploying ransomware, the agencies added.
How to Mitigate BlackCat Affiliate Attacks
The advisory highlighted a range of measures to tackle the common approaches employed by BlackCat affiliates. These include:
- Secure remote access tools by implementing application controls to manage and control execution of software
- Implement phishing-resistant MFA, such as FIDO/WebAuthn authentication
- Use network monitoring tools to identify, detect and investigate abnormal activity and potential traversal of the indicated ransomware
- Adopt internal mail and messaging monitoring to identify suspicious activity
- Employ user awareness training on how to identify social engineering and phishing attacks
BlackCat Reportedly Behind Change Healthcare Incident
The BlackCat group has reportedly claimed responsibility for the ongoing cyber-attack against Change Healthcare, stating on its dark web site that it exfiltrated 6TB of data from the firm. However, the claim was subsequently removed without explanation.
Change, which has merged with Optum, a subsidiary of healthcare giant UnitedHealth Group, is still experiencing disruption to its services more than a week after the attack was first reported.
UnitedHealth has access to around one-third of US patients and handles 15 billion healthcare transactions annually.
In a filing to the US Securities and Exchange Commission (SEC), UnitedHealth said the attack was perpetrated by a “suspected nation-state associated cybersecurity threat actor.”
Change said it is working on multiple approaches to restore the impacted environment, “and will not take any shortcuts or take any additional risk as we bring our systems back online.”
The incident has disrupted healthcare services, including prescriptions, throughout the US.
The American Pharmacists Association (APhA) reported on February 23 that many pharmacies throughout America could not transmit insurance claims for their patients as a result of the incident.
