ALPHV was the second-most leveraged ransomware strain in North America and Europe between January 2022 and October 2023, just before the reported takedown of the group’s website, according to ZeroFox research.
The analysis found that ALPHV, aka BlackCat, accounted for around 11% of all ransomware and digital extortion (R&DE) attacks in North America over the 21-month period. This was second only to the LockBit collective.
ALPHV was also the second-most leveraged ransomware strain in Europe, accounting for 6% of all threats.
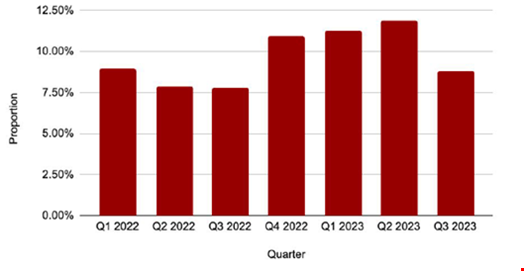
Additionally, the report found that ALPHV’s global activities increased significantly in 2023 compared to 2022, although there was a drop-off in Q3 2023.
The group’s biggest focus over the period was on organizations in North America, making up 56% of their attacks. This was followed by Europe, at 20%.
How Will ALPHV be Impacted by Rumoured Disruption?
Earlier this month (December 2023), it was reported that the ransomware-as-a-service (RaaS) gang suffered online disruption which intelligence experts have attributed to law enforcement action.
While the disruption is welcome, Daniel Curtis, Senior Intelligence Analyst at ZeroFox, emphasized that website outages are a fairly regularly occurrence for cybercrime groups, and will likely only result in a temporary suppression of the threat from its operatives.
“The extortion cartel’s blog is currently experiencing long periods of downtime, which happens from time to time in these ecosystems and is usually the result of an undisclosed law enforcement operation, inter-cartel strife, or network maintenance,” he noted.
Curtis added that in the unlikely event ALPHV affiliates are no longer able to deploy the strain, they will quickly pivot to other R&DE offerings to continue targeting victims.
ALPHV Intrusion Vectors
ZeroFox researchers identified a range of techniques used to deploy the ALPHV strain over the period:
- Exploit Internet-Facing Applications. These encompassed a range of vulnerabilities, including remote code executions, privilege escalations and access controls.
- Social engineering. Various social engineering techniques, such as spear phishing, vishing mass malicious communications were used to allow threat actors to deliver and execute the malware remotely.
- Malware-as-a-Service (MaaS). ALPHV affiliates were observed leveraging the MaaS Emotet in order to initiate first-stage system breaches.
- External Remote Services. Attackers exploited Remote Desktop Protocol (RDP) to access victim networks by leveraging legitimate user credentials.
- Drive-by Compromise. Some affiliates gained access to a system via a user visiting a website over the normal course of browsing, with the user’s web browser typically exploited for exploitation.
- Valid Accounts. Attackers have used compromised credentials to bypass access controls, establish persistence, escalate privileges, and evade detection.
Update 19/12/2023: It has now been confirmed that ALPHV's website is down as a result of law enforcement action. A statement on the group's website currently reads: 'The Federal Bureau of Investigation seized this site as part of a coordinated law enforcement action taken against ALPHV Blackcat Ransomware.'
