Conficker was one of the biggest causes of the rise in worm volumes. The worm, released in late 2008, took advantage of an already patched vulnerability listed in Microsoft security bulletin MS08-067.
"We saw Conficker hitting the enterprise considerably more than it hit consumers", said Jeff Williams, principal architect at the Microsoft Malware Protection Center. "I owe that to the fact that consumers tend to turn on automatic updates, whereas enterprises tend to have their own timeline where they do patches and deployment."
Usage of Microsoft Update (the automatic update service covering multiple Microsoft products) has increased significantly in the past three years, according to the report, but this is largely consumer-targeted. The number of Windows Server Update Services or Microsoft System Center management products installed grew faster than the Windows installed base until the second half of last year, but has flattened out and grew at the same rate as the Windows installed base in the first half of 2009.
However, it isn't just patch deployment that affects the ability of worms to spread in the enterprise, Williams said. Enterprises tend to have more networked machines, which can serve as infection vectors. Mapped network drivers were the infection vector for another network worm called Win32/TaterF, which along with Conficker was responsible for the 98.4% rise in worm infections seen during the first half of this year. The worm, which targets players of online games, did particularly well in Korea and Spain. Brazil also suffers heavily from worms.
The large numbers of worm infections is particularly significant given the relatively small number of unique samples collected by the company. 2.7 million worm samples were collected in the first half of 2009, compared to 23.5 million trojans.
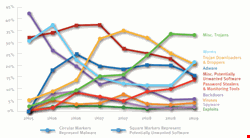
In the US, miscellaneous trojans were still by far the biggest category of infections, followed by trojan downloaders and droppers. Worms came a close fifth, after adware, and miscellaneous potentially unwanted software. Win32/FakeXPA was the most prevalent infection in US companies. It is a rogue antivirus trojan that claims to scan for malware, and then tries to charge the user to remove nonexistent threats.
The report also suggested that Windows Vista was far less heavily infected than its predecessor. The infection rate for the release to manufacturing version of Vista [before a service pack was applied] was around five percent, compared to the 33% infection rate for Windows XP when first released.