Infosecurity News

TalariaX Receives Renewed Certification as RSA SecurID Partner
Singapore-based TalariaX, and its sendQuick appliance-based SMS gateway, will continue as a SecurID partner for RSA Authentication Manager 8

One-in-Five 9–11 Year-Old Children Admit to Meeting a Stranger They Speak to Online
Today is the first day of Get Safe Online Week 2013, "an annual awareness campaign organized by Get Safe Online (GSOL) to reinforce the fact that people can stay online safely just by following some simple precautions." But neither adults nor children are yet doing so.

The RU:8080 Gang Kicks Off a New Dropbox Password Reset Campaign
Email scams are often given away by poor grammar and typos. AppRiver, however, has discovered a new scam that looks more than usually professional. It's an email that says, "You recently requested a link to reset your Dropbox password. The old one is now marked as "dangerous".

2014 SANS Training Calendar Announced
The SANS Institute has announced an enhanced calendar of training events across Europe for 2014.

Data Breach at Royal Vet College Prompts ICO BYOD Warning
In the wake of a data breach at the Royal Veterinary College, the UK’s Information Commissioner’s Office (ICO) is warning organizations they must make sure that their data protection policies reflect how the modern workforce are using personal devices for work.

Cyber Security Challenge and WSS Celebrate Female Code-breakers at Bletchley Park
On Friday 11th October 2013, veterans, women in top security positions and the next generation of cyber defenders met at the home of British code-breaking, Bletchley Park.

Oracle Update Adds Java and Patches 120 Flaws
Oracle has released its Critical Patch Update (CPU) for October 2013, incorporating, for the first time, Java, which was heretofore patched on a separate cycle every four months. The update is massive, fixing 120 flaws across most of Oracle’s product families.

DDoS Attacks Getting Harder to Detect
Distributed denial-of-service (DDoS) attacks are getting harder to identify, and they will most likely be found to originate in Indonesia or China, new research has shown.

A Q&A with Charlie Miller, Computer Security Researcher at Twitter
At the recent Hacker Halted conference in Atlanta, Infosecurity Editor Eleanor Dallaway, spoke to Twitter’s computer security researcher, Charlie Miller, also known for his public hacks on Apple products and his tenure at the NSA. They talked about mobile threats, car hacking and the evolution of the information security industry’s mindset.

Hackers Target Mandiant CEO Via Limo Service
Hackers are apparently stalking Kevin Mandia, chief executive of the cybersecurity company Mandiant.

Google-backed File-sharing Service Spreads Chinese Malware
Most people in the West haven’t heard of it, but Xunlei, a file-sharing service that boasts Google as an investor, has hundreds of millions of users in China. And, it was recently found to be distributing a signed malware known as KanKan.

LockLizard Expands Document DRM Market to Android Devices
LockLizard, a London-based provider of PDF document digital rights management (DRM) controls, is in the final stages of delivering a DRM secured viewer for the Android device marketplace.

CryptoLocker: The Ransomware There's No Coming Back From
A ransomware threat known as CryptoLocker is making the rounds, scrambling files in the process. And once it’s triggered, there is no way to recover them.

Google Chrome Opens Up Personal Information to Hackers
Google Chrome has been shown to have a major security flaw: any consumer who has ever typed in personal information while using the Google Chrome browser, be it for e-commerce or to sign up for newsletters, should be aware that this information is saved to their hard drives, unencrypted.

Public WiFi Hotspots Ripe for MITM Attacks
Ah, the public hotspot: oases of connectivity in airports, coffee shops, bookstores, town centers and at chains that range from Starbucks to Barnes & Noble to McDonalds.

Nordstrom Hit By Card Skimmer Scam
The retail sector often faces unique security challenges, not the least of which are the point of sale (PoS) terminals and cash registers that offer a convenient repository from which to lift credit and debit card numbers. Hackers can make use of connected PoS terminals to get in virtually, or can compromise physical security to get ahold of the information they want.

Blue-chip Hacking List Scandal Grinds On
The blue-chip list is a list of around 100 major firms and a few celebrities that employed four disgraced – and imprisoned – private investigators. The 'scandal' is that SOCA sat on the list without ever revealing its content, and possibly without adequately investigating the PI clients concerned.

Google Offer OSS Patch Bounty to Fixers
More and more software companies – including Google – have started to offer bug bounties to independent security researchers who find and responsibly disclose software flaws. Now Google will offer a bounty to OSS developers who also fix them.

vBulletin Exploit Makes the CMS Rounds
vBulletin, one of the most popular content management systems (CMS) on the web and the engine behind many a discussion forum, is the target of a new exploit making its way into the wild.
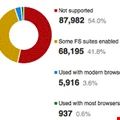
SSL Forward Secrecy Now Included in SSL Pulse Reports
SSL has long been used to provide security in communications; and Ivan Ristic, director of engineering at Qualys has long been an enthusiast. Last year, with the Trustworthy Internet Movement, he was instrumental in establishing SSL Pulse, "a continuous and global dashboard for monitoring the quality of SSL support across the top one million web sites."



