A China-aligned hacking group known for its global cyber espionage campaigns has been observed deploying an undocumented network implant that it uses to conduct adversary-in-the-middle (AitM) attacks.
The group, PlushDaemon, has been active since at least 2018 and has targeted organizations in Cambodia, South Korea, New Zealand, the US, Taiwan and even Hong Kong and China.
While the group’s main initial access vector is hijacking legitimate updates of Chinese applications, it was identified as the culprit behind a supply chain attack targeting IPany, a South Korean VPN company, in May 2024.
While investigating the group’s techniques, tactics and procedures (TTPs) in 2024, ESET researchers discovered an Executable and Linkable Format (ELF) file, called bioset, submitted to VirusTotal that contained two subdomains from PlushDaemon’s infrastructure.
The researchers analyzed the suspicious file, internally named dns_cheat_v2 by its developers, and found that it was a new AitM tool that forwards domain name system (DNS) traffic from machines in a targeted network to a malicious DNS node.
This allows the attackers to redirect the traffic from software updates to a hijacking node that serves instructions to the legitimate software to download a malicious update.
Once inside, the PlushDaemon operators drop two downloaders, LittleDaemon and DaemonLogistics, which deliver a backdoor toolkit designed for cyber espionage operations.
“These implants give PlushDaemon the capability to compromise targets anywhere in the world,” wrote the researchers.
The researchers codenamed the tool EdgeStepper and provided a malware analysis in a report published on November 19.
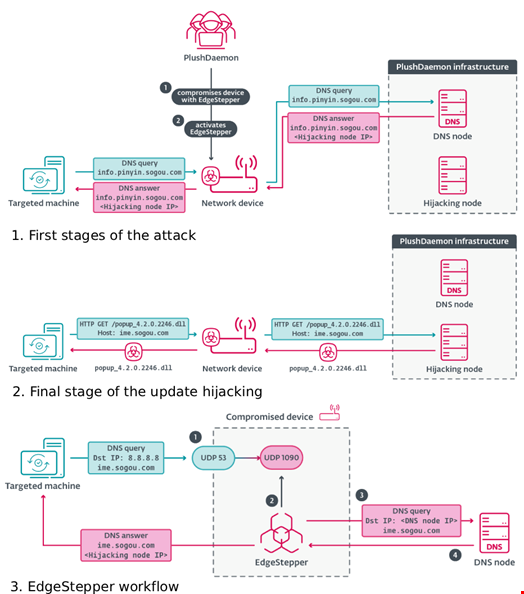
“It is important to note that it is unlikely that EdgeStepper is the only component deployed on the compromised network device. Unfortunately, we don’t have samples of other components in the compromise chain,” the ESET researchers wrote.
In the 2024 cyber-attack against IPany, PlushDaemon was observed using another piece of malware, a Windows backdoor with a toolkit of over 30 components dubbed SlowStepper by ESET.
