Running a secure, efficient and scalable application on Amazon Web Services (AWS) is a daunting task for organizations that are migrating to the cloud. AWS developed the Well-Architected Framework to help cloud architects build secure, high-performing, resilient, and efficient infrastructure for their applications. The framework is based on five pillars - operational excellence, security, reliability, performance efficiency, and cost optimization.
In this article, we will focus on the security pillar, providing an overview of the design principles and five focus areas that define what security in the cloud is composed of on AWS.
These principles form the foundation of the AWS Security Pillar but are foundational security concepts for any cloud security strategy regardless of the cloud hosting provider.
Design Principles
Within the AWS Security Pillar, AWS describes seven design principles that assist cloud architects with securing their applications:
- Implement a strong identity foundation
- Enable traceability
- Apply security at all layers
- Automate security best practices
- Protect data in transit and at rest
- Keep people away from data
- Prepare for security events
Of these seven design principles, 'automating security best practices' should be near the top of any modern cybersecurity decision-makers’ list of priorities. The cybersecurity skills shortage is well researched and well-reported throughout the cybersecurity industry, so automating security best practices helps organizations gain efficiencies in their cybersecurity program’s.
For example, as I am sure FedEx and Wal Mart would agree, allowing unlimited access to S3 buckets storing sensitive information is a costly mistake. However, this is a common misconfiguration that can be corrected without burdening valuable human resources by implementing the automating security best practices design principle.
If you’re using AWS, organizations can leverage services such as AWS Config, Cloud Watch, Cloud Trail and Lambda to detect when buckets are publicly available and remediate these buckets by making them private before a bad actor can take advantage of the misconfiguration. The design principles lay the foundation for the five focus areas of this security pillar.
Focus Areas
AWS outlined five areas that encompass security in the cloud:
- Identity and access management
- Detective controls
- Infrastructure protection
- Data protection
- Incident response
Figure 2 below displays the AWS services that are utilized to address each of these focus areas. These services were built specifically to perform security functions such as logging, identity management or encryption for AWS resources.
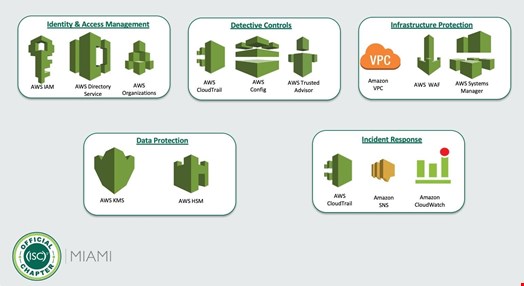
When examining these five focus areas, security practitioners should look at each focus area as an integrated component of their security program, not individual siloed processes. There is overlap through many of these areas and it is important to consider how each focus area can build on or influence others.
An example of this is with the detective controls and incident response focus areas, as an organization detects potential security trends or events this will automatically feed the incident response process. The graphic above shows how AWS CloudTrail is a service that impacts the detective controls and incident response focus areas.
AWS CloudTrail is a governance, log management and auditing service on AWS that records all actions on a given AWS account. Implementing logging is table stakes in any cybersecurity program, you have to know what actions are taking place in your account to identify any security events that could impact your commitments to your customers.
In an incident investigation, you also need logs to help look back and assess the details of the incident. During the incident response process, logging is an easy way to determine when the event occurred, where the attacker came from, how long the attacker was in the system and the resources that were impacted. There’s more that logging can do to support incident response and there are many other examples that show how focus areas are intertwined and should be used to support each other in a mature cloud security program.
The Security Pillar of the AWS Well-Architected Framework is a great start for any security practitioner looking for the “answers to the test” on how to secure their cloud-hosted application.#
Cloud security is top-of-mind for every executive moving their workloads to the cloud or managing an existing application on the cloud. Evaluating an existing or planned application against the Security Pillar principles can assist you in determining whether your organization has implemented basic cloud security concepts at its foundation and guide what actions to take to improve deficiencies.
AJ Yawn is a cloud security subject matter expert that possesses over nine years of senior information security experience and has extensive experience managing a wide range of compliance assessments (SOC, ISO 27001, HIPAA, etc.) for a variety of SaaS, IaaS, and PaaS providers.
AJ spent over five years on active duty in the United States Army, earning the rank of Captain. AJ has earned several industry-recognized certifications, including the CISSP, AWS Certified Security Specialty, AWS Certified Solutions Architect-Associate, and PMP. AJ is involved with the AWS training and certification department, volunteering with the AWS Certification Examination subject matter expert program.
AJ graduated from Georgetown University with a Master of Science in Technology Management and from Florida State University with a Bachelor of Science in Social Science.
