
The new year is always a time of reflection, regrets and resolutions. What can we do better? What should we not do? What unforeseen events will test us in the coming year?
In the high-anxiety world of network security, these questions are more important than ever as we face the dual challenge of dealing with more attacks at higher speeds that threaten the most important commercial platform of the 21st century – the internet.
The Internet Under Attack
In the space of a couple of decades, the internet and IP networks in general have transformed from their roots as a handy way for researchers to share information. There is not a single sector of our lives untouched by the internet – we use it for work, for play, to pay our bills, to purchase our goods, and to access government services.
The basis for this success is the open standards and ease of adoption and adaptation of IP technology. These are exactly the advantages, however, that have become disadvantages of late. The internet is now under attack from highly organized cybercriminals who have realized that without global cooperation on cybercrime, it is difficult for national law enforcement agencies to respond.
To date, this activity has confined itself to data loss, such as theft of credit card information and social security numbers. There is, nevertheless, potential for more serious damage as the internet becomes more pervasive.
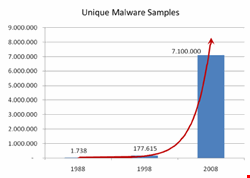
To understand the scope of the network security challenge, consider figures from Trend Micro, a leading provider of network security solutions, which reported an explosive growth in the number of unique malware samples (i.e., types of attack) over the last 20 years. Figure 1 shows this alarming development.
Network security system vendors are struggling to respond to these new attacks as quickly as they occur. In a sense, they are playing a cat-and-mouse game with adversaries who are at least as innovative at exploiting weaknesses in networks and applications as they are at detecting attacks.
The High-Speed Cybercrime Pursuit
Higher data rates compound the challenge facing network security system vendors. IP networks are now being upgraded from 1 Gbps to 10 Gbps link speeds, with 40 Gbps and 100 Gbps on the horizon. At 1 Gbps, a network security system needs to analyze up to 1.5 million packets per second. At 10 Gbps, this becomes 15 million packets per second. This is per port and only in one direction!
The challenge for network security system vendors is to ensure that their systems:
- Can handle up to 15 million packets per second per port in each direction
- Have the necessary processing power and memory to analyze packets in real-time
- Can scale to detect millions of new malware samples and higher line rates
Scaling Network Security Systems
The traditional approach to building network security systems is to build customized hardware including ASIC chip development. However, with the exponential growth in malware and higher line rates, network security systems need to scale, on a regular basis, in both terms of data handling and computing power. This in turn means that the lifetime of a product revision will be shorter.
This begs the question: Can network security system vendors keep up, and have they got the deep pockets required to fund custom hardware and chip development on a regular basis?
It also leads to the question: Is there another way?
High-performance network security systems can be based on standard, off-the-shelf PC servers when these are combined with intelligent, real-time network analysis adapters for handling full line rate data. The benefit of this approach is that it takes advantage of the strong roadmap of PC server and CPU chip vendors that are updating their performance and the number of processing cores they support on a yearly basis.
Get Smart and Address the Dual Challenge
We need to get smarter and focus our energies where they have most effect to address the dual challenges facing network security. Using off-the-shelf hardware to keep up with processing needs and line rates is smart. It also allows efforts to be directed at what really matters; the smart network security algorithms that can foil the efforts of cybercriminals.
Make sure in 2012 you can say “Regrets, I have a few…but too few to mention!”
Daniel Joseph Barry is VP of marketing at Napatech and has over 17 years of experience in the IT and telecom industry. Prior to joining Napatech in 2009, Dan Joe was marketing director at TPACK, a leading supplier of transport chip solutions to the telecom sector. He has an MBA and a BS in electronic engineering from Trinity College Dublin.