Objectively assessing the performance of anything can be extremely difficult. Standards and guidance can be put in place to help, but for many things, the potential of subjectivity creeping in remains intact, leaving us with an expected margin of error. What we are willing to accept as a margin of error and the downstream effects are important considerations that need to be made.
Take the Winter Olympics in Beijing. During the men’s halfpipe snowboarding competition last week, Ayumu Hirano of Japan delivered an incredible performance – one that was immediately speculated to throw him into first place when considering the scoring framework in place. The judges were shocked and disappointed when the score was released, putting him in second place. He delivered an even more incredible run on his next attempt, which catapulted him into first. He went on to win gold. If he would not have delivered an additional (and killer) run, Hirano would have achieved silver and may have spent the rest of his life wondering, “what if the judges would have scored this differently?”
So, what does this have to do with security? There are parallels in our comfort level with our email security controls, particularly secure email gateways or SEGs as they are more commonly called. For years, SEGs have been the go-to technology for blocking threats delivered via email from reaching your employees’ inboxes. Just as we look to the judges at the Olympics to deliver fair and justifiable scores, we expect SEGs to protect our organizations against the ever-advancing tactics and techniques of attackers. We become comfortable that SEGs are the authority for stopping email-borne threats and we trust what they say to be true. We even trust when some market-leading SEGs claim to have a 99.99% efficacy rate stopping attacks.
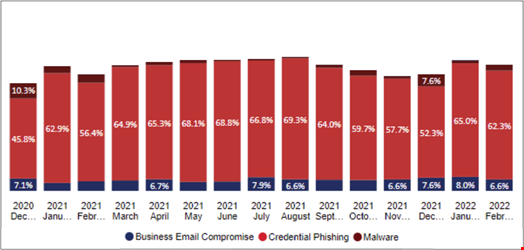
Cofense, a phishing defense vendor, has a unique view into the threats bypassing all types of security controls and configurations present in our customer’s environments. Of the millions of emails analyzed over 2021, our team noticed malware typically delivered as an attachment was not commonly showing up. As you see below in Figure 1, what was showing up was the more credible and harder-to-spot threats such as credential phishing and a steady rate of business email compromise (BEC) attacks. Threat removed and threat unavailable indicate the threat unable to be further analyzed due to quick takedowns.
If we are looking at upwards of 99% efficacy rate of SEGs, why are we still seeing millions of threats making it through to our clients’ inboxes? This was the headscratcher moment of 2021 for us that led us down the route of answering the question, “Where’s the truly objective analysis of secure email gateways?”
Utilizing advanced real, active phishing indicators, we tested the efficacy of multiple SEGs in many customer environments to understand what was being caught and what was slipping through. The type of indicators sent through is of utmost importance here because this is the aspect that provides visibility into the actual performance of the SEG when it comes up against both traditional and more advanced types of phishing attacks. We used phishing links, imposter emails and attachment-based threats.
Here is a sample of some specific, live phish we tested:
- Internal and external impersonation attempts leading to business email compromise (BEC) or CEO fraud
- Brand impersonation
- Impersonation via SaaS programs
- Phishing links inside attachments
- Inline HTML attachments
- Brand phishing pages and phishing kits
Continuous testing of some of the most popular SEGs over a six-month period jived with the volumes and threat types we saw in customer environments. For simplicity’s sake, results are broken down into two attack types – attacks that contained malicious URLs that reached the inbox and those that were attachment-based.
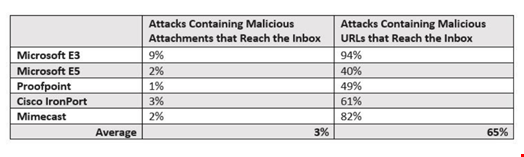
Results speak for themselves. When we think of traditional attachment-based phishing attacks – on average, only 3% of these types of attacks are making it to the inbox in SEG-protected environments. When we think about more advanced types of attacks using malicious URLs, performance dwindles, with about 65% of threats on average making it to the inbox. Or, said another way, only about 35% of live, active URL-based attacks were stopped. These are the types of attacks that may send employees to an external site to input credentials – the types of attacks that we have seen lead to successful ransomware attacks.
Knowledge is power, and so is objective and transparent scoring. So whether you are taking part in the Olympic Games or trying to make informed decisions about your email security controls, removing as much subjectivity as possible will lead to more confident outcomes and a clearer path to gold.

