Many organizations deliver mandatory security awareness training to their staff on an annual basis. Solutions in the market to support this have tended to focus, almost exclusively, on ‘training’ users rather than actually changing their behavior.
An underlying compliance driver for the deployment of security awareness solutions is unquestionably part of the reason, but it often feels like the success criteria is “have I delivered training to users?” rather than “have I changed the security behavior of users (and therefore reduced the risk to my business)?” However, security behavioral change is achievable.
Nudge, Nudge
Standard economic theory used to hold sway in its suggestion that we make decisions in a purely rational, selfish way. It is now well-established that the reality is somewhat more complicated than that. Over the last two decades, psychology and, in particular, behavioral economics have been popularized by researchers such as Kahneman and Thaler/Sunstein – with Thaler receiving a Nobel prize for his contributions on Nudge Theory, a behavioral theory which uses positive reinforcement to influence behaviors. Stanford Professor BJ Fogg’s behavioral change model is also worthy of mention as applicable in a security awareness context.
The Behavioural Insights Team, often known as the ‘Nudge Unit,’ was set up by the UK government to apply nudge theory to try to improve government policy, government services and to save the UK government money. They summaries their approach in the EAST® framework which focuses on delivering behavioral change by making the desired action Easy, Attractive, Social and Timely (EAST®).
- Easy – is the behavior easy to do, simple to understand, is it the default, do targets of the behavioral change have the capability?
- Attractive – is the behavior something targets want to do, are they motivated, incentivized, is their attention attracted?
- Social – is this something others do, can I get mutual support, can networks amplify the effect we are trying to achieve?
- Timely – is the target suitably prompted, at a time they are most receptive, to effect the required behavior change?
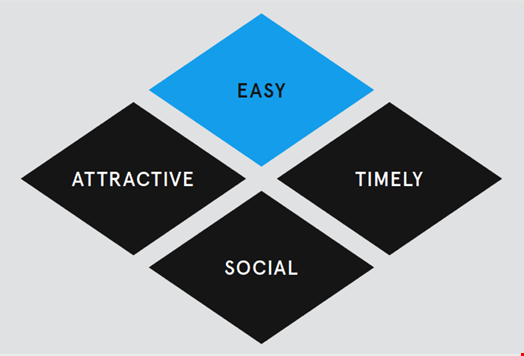
Image Source: Behavioural Insights Team (PDF)
EAST® image used with permission ©Behavioural Insights Ltd. Not to be reproduced, copied, distributed or published without the permission of Behavioural Insights Ltd.
Increasing Vigilance and Reporting Phishing
Let’s look at one aspect of security awareness through the lens of this model: increasing vigilance and reporting suspicious emails. Key to preventing phishing is both a healthy skepticism, and users pausing to think before acting on an email. One of the best behaviors to encourage in users, that supports thinking before they click, is to report suspicious emails. However, most IT/Security teams don’t have time to respond and without a reward for good behavior, users stop reporting.
How can we change end-user behavior such that they think before clicking links and report suspicious emails?
Applying the EAST® model offers some answers.
Make it Easy
Easy to remember: Deliver low friction reminders about phishing on a regular basis. Keeping phishing ‘front of mind’ as well as highlighting what to look out for. Note that we don’t need to turn users into experts, just help them stay vigilant and know what to look out for.
Easy response: Offer a simple reporting email address e.g. phishing@thinkcyber.co.uk.
Make it Attractive
Attract attention: Make the low friction reminders interesting and engaging.
Provide a reason: Explain the impact on the business but also explain why this is important in a personal context which is typically more powerful. Using stories and real examples of phishing based breaches attract interest.
Make it Social
Exploit social proof: Highlight emails reported by other employees. Create a mindset of “if others are doing it, so should I”, reward people for reporting through feedback. Make it real showing real examples hitting the organization.
Make it Timely
Timeliness is key: The best prompts are made at the ‘opportune moment’. Prompting when users are in their email or on risk indicators such as an unknown sender.
Importantly, without prompts, don’t expect behavior change to happen, a point that BJ Fogg takes even further. Periodic awareness training is a poor prompt. And awareness delivered having tricked employees with a phishing test may not be well received or remembered.
And if you’re wondering how prompts can be delivered at that particular point in time then you’ve stumbled on the reason we developed our real time security awareness product Redflags™!
In summary, true behavior change isn’t as easy as it looks. But considering the EAST® model and other behavioral change theories when designing a Security Awareness program might be a good first step. At ThinkCyber we believe that delivering the right content, in the right way and at the right time really can drive towards secure behavioral change.
“EAST” and the Easy, Attractive, Social, Timely diamond graphic are registered trademarks of Behavioural Insights Ltd.
ThinkCyber are a Cyber Security start-up focusing on delivering pragmatic, user centric solutions to cyber security challenges. Working alongside academics from UCL and Northumbria University and with InnovateUK support, they have created their RedFlags™ product. A software toolkit designed to drive secure behavior change by delivering ongoing and timely security awareness interventions across a range of threats from phishing to data handling, as well as providing security teams with full visibility of user engagement, completion rates, content dwell times and risky behaviors.
Empower your users to protect themselves against cyber threats. Find out more at thinkcyber.co.uk.
You can discuss your behavior change needs in person with Think cyber Security Ltd on Stand X47 at Infosecurity Europe in London from 4-6 June. Infosecurity Europe is the leading European event for information and cyber security; find out more and secure your free visitor badge.