A total of 26,447 vulnerabilities were disclosed in 2023, surpassing the previous year by over 1500 CVEs.
The figures come from the latest report by the Qualys Threat Research Unit (TRU), published today.
Notably, less than 1% of these vulnerabilities posed the highest risk, being actively exploited in the wild by ransomware, threat actors and malware.
Key findings revealed that 97 high-risk vulnerabilities, likely to be exploited, were not part of the CISA Known Exploited Vulnerabilities catalog. Additionally, 25% of high-risk vulnerabilities were exploited the same day they were published.
The deep dive into the vulnerability threat landscape also highlighted that over 7000 vulnerabilities had proof-of-concept exploit code, while 206 had weaponized exploit code, increasing the likelihood of successful compromises.
The report revealed that 32.5% of high-risk vulnerabilities affected network devices and web applications, emphasizing the need for a comprehensive vulnerability management strategy.
The Qualys TRU also shed light on the mean time to exploit high-risk vulnerabilities in 2023, standing at 44 days.
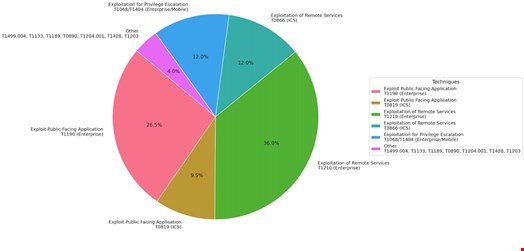
Top MITRE ATT&CK tactics and techniques used in exploits include the exploitation of remote services, public-facing applications and privilege escalation.
Among the most exploited vulnerabilities are CVE-2023-27350 in PaperCut NG and CVE-2023-0669 in Fortra GoAnywhere MFT.
Read more on CVE-2023-0669: Clop Ransomware Group Exploits GoAnywhere MFT Flaw
Threat actors, such as TA505 (also known as Cl0p Ransomware Gang) and malware like LockBit and Clop, played significant roles in high-profile cyber-attacks, exploiting zero-day vulnerabilities and emphasizing the need for enhanced cybersecurity measures.
As organizations grapple with the dynamic nature of cyber-threats, the Qualys TRU recommends a multifaceted approach to vulnerability prioritization, focusing on known exploits in the wild, those with a high likelihood of exploitation and those with weaponized exploit code available.
“The imperative of this report is for organizations to assess their strategies for threat mitigation and threat remediation. Threats are growing in volume and velocity, making automation critical for organizations to reduce their mean time to exploitation,” commented John Gallagher, VP of Viakoo Labs at Viakoo.
“Best practices must be followed to stop lateral movement and RCE [remote code execution] across the organization.”
These include implementing effective network segmentation that considers all devices and applications, automating patching and password rotation across fleets of devices, and extending zero trust principles to all network-connected systems.
