At the (ISC)2 Congress in Dublin, Ireland, on October 19, security analyst Megha Sharma presented her research and risk assessment of the three key areas in a smart city
In order to implement efficient controls in smart cities, Sharma tells Infosecurity, “you need to understand the systems and their challenges.” The study focusses on the risks of the three major areas in a smart city - smart energy, smart transport and open data – and how they should be approached from a security and risk perspective.
Sharma explains a smart city as a “city that uses the internet and communication technologies to overcome the issues faced in a conventional city, such as traffic congestion, over-population and energy sustainability.”
The first step in assessing a smart city’s risk is characterizing it, says Sharma. Is it a virtual city, a knowledge-based city, a broadband city, a mobile city, a digital city, an intelligent city, a ubiquitous city or an eco-city? “No smart city is similar to another one. So as the cities and technologies differ, so do the controls.”
Using Bristol, UK, as an example, Sharma delves deeper into the risks associated with smart transport, smart energy and open data.
Smart Energy
Sharma declares smart energy the most valuable element of a smart city, but admits it has the highest risk factor, with most of the threats posing high risk to the assets.
Smart energy produces huge sets of data, and one of the biggest challenges is maintaining that data confidentiality. “The data usage needs to be monitored to ensure it is being used in the right way. It’s important to consider who has access to that data, as there are a lot of third-parties involved, and ensure that the data is tamper-resistant.”
Auditing should be transparent, Sharma tells Infosecurity, giving an example: “Users want to use off-peak energy consumption to save money, which is an incentive of a smart city. However, energy providers could modify that data to benefit their own profits. Service providers should be monitored, audited, and made to be transparent with their data and pricing.
Sharma adds that people need to be educated about that data usage and how it effects their privacy.
Sharma also points to the issue of smart energy data availability, which she calls “a crucial issue. In the case of a DDoS attack, availability of services must be maintained,” she insists.
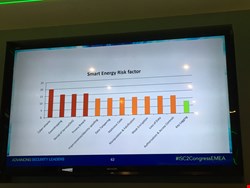
Traditional cyber-attacks are the biggest risk to smart energy. (See slide 1 for further risk factors).
Smart Transport
Smart transport brings its own risks; some which are already issues, and some that will be in the future. The concern, Sharma points out, is around traffic safety and accidents.
Scalability is an issue, as the number of vehicles on the roads is increasing and eventually, cars will be able to securely interact with each other. “This would require a privacy certification program to authorize the user in the car to stop adversary from connecting. It would verify that A is A and B is B,” she explains.
“Most vehicles connect to wifi when moving, but the challenge is to collect data from people and provide seamless services to them regardless of communication links.” Additional considerations, she continues, are the volatility of links when distance is increased, and GPS spoofing.
Sensor networks are so extensive that patch management and power supply is a big issue, Sharma explains. “Efficient monitoring of sensors and traffic signals is a challenge due to the huge number of sensors and the weak communication networks.”
Patching sensors is highly expensive, and as yet, there is no solution. “Smart cities will connect to other smart cities to create a network. Imagine how many sensors there will be!” exclaims Sharma.
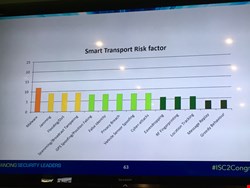
Malware and jamming are considered the biggest risks for smart transport. (See slide 2 for further risk factors).
Smart Data
The advantage of smart open data, Sharma explains to Infosecurity, is transparency. “For example, if data is published with statistics on where crime is happening, this would help citizens to stay safe.”
There is a concern around accuracy of open data, however. “Accuracy is hard to determine and verify as open data is open to all and you can’t necessarily trust who uploaded that data.” Accessibility, privacy and legislation violation are all additional concerns.
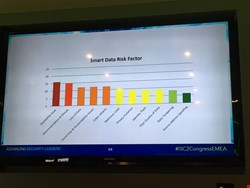
The greatest smart data risk factor is availability, followed by misinterpretation and misuse. (Please see slide 3 for further risk factors).
Who is Ultimately Responsible for the Security of a Smart City?
Councils are held responsible for the policies and security of a smart city, advises Sharma, telling Infosecurity that they recruit experts from industry and academia.
Ultimately, the success of a smart city comes down to whether or not the population are tech-savvy, educated and ready to embrace their smart city. “If the population of a city isn’t properly educated or ready, it would be a disaster,” she says. To the contrary, Bristol has been a success due to its high university population and tech readiness.
Councils are trying to organize training and educational programs for citizens to interact with, and provide access to online documentation.
Worst-Case Scenario
The worst-case scenario of a security incident in a smart city is ultimately loss of life, explains Sharma. “With smart transport, if two cars are interacting and there’s a jamming of that communication, it could result in loss of life.”
A more likely scenario though, is criminal exploitation of the knowledge of a person’s daily activities and behaviors which are discoverable through smart energy.
In conclusion, Sharma argues that we can gain more from smart cities than we can lose. “Half the problem will be eliminated if we educate the citizens about smart cities and how they can be more secure and control their own data.”
