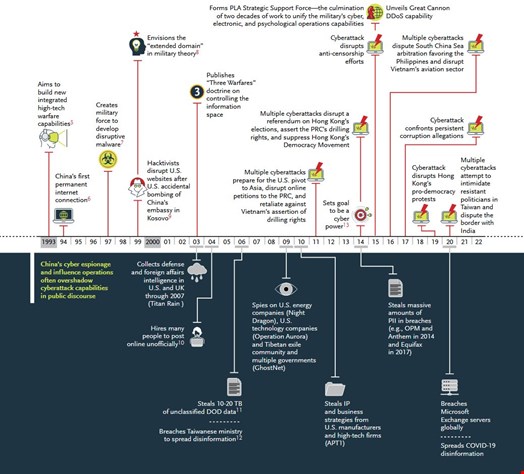
Chinese state-sponsored cyber-attacks pose a growing threat to US national security, according to a report from consultancy firm Booz Allen Hamilton released on October 12, 2022.
The report, Same Cloak, More Dagger: Decoding How the People's Republic of China (PRC) Uses Cyber Attacks, is addressed to CISOs of American companies and their allies as well as threat analysts. It offers a comprehensive analysis of more than 13 case studies of Chinese-sponsored cyber-attacks over the past decade to understand “the conditions that ignite PRC cyber offensives,” which will allow organizations to “better anticipate when, where, and how those attacks may occur” and “ensure they are ready to defend against them.”
The case studies are divided into two groups, each sub-divided into two themes:
- Threats to domestic interests: ‘Foreign Information Threats’ and ‘The Hong Kong Democracy Movement’
- Threats to foreign interests: ‘Competing South China Sea Claims’ and ‘Indo-Pacific Competition’
“[Their findings] show that China is developing and deploying cyber-attack capabilities to advance its national ‘core interests.’ These cyber-attacks complement China’s better known, increasingly assertive, and diverse attempts to advance its interests online through legal, financial, cultural, political, and technical means.”
However, Booz Allen added that the report was exclusively based on open-source research. “The true measure of China’s cyber-attack capabilities […] likely cannot be fully discerned in open sources. It is possible China has chosen to not deploy its full capabilities or it has done so without public attribution,” reads the report.
On top of the case studies, the report provides an overview of Chinese security and intelligence agencies, an assessment of their motives, a timeline of Chinese cyber activity since 1993, a catalog of threat actors and their common tactics, techniques and procedures (TTPs) as well as recommendations for CISOs and threat analysts.