In May 2021, the UK’s National Cyber Security Centre (NCSC) published its Connected Place Cyber Security Principles to help authorities build awareness and understanding of the security considerations needed to design, build and manage their connected places – or smart cities. Its recommendations will help ensure the security of underlying infrastructure, making it more resilient to cyber-attacks and easier to manage.
A connected place provides a range of critical functions and services to its citizens, which rely on moving, processing and storing sensitive data, as well as controlling critical operational technology. Examples include traffic management, CCTV, transport services, healthcare and emergency services.
This makes such systems an attractive target for threat actors. If compromised, the consequences could impact local citizens, ranging from privacy breaches to disruption or failure of critical functions.
But it is not just authorities that need to embrace the scope of these principles to mitigate risk. Other stakeholders include equipment and service suppliers, such as telecoms and transport providers, blue light and rescue services, critical infrastructure and utilities and landlords and citizens.
There May Be Problems Ahead
Authorities will face challenges related to budgets and how to apply security principles to existing multi-year contracts and preinstalled systems that don’t currently comply with the principles.
Another challenge is the availability of skilled resources to assess, quantify and drive implementation, particularly among SMEs.
Then there is the issue of complex supply chains and interconnected systems, involving multiple manufacturers and suppliers. This may be compounded by a lack of engagement from service providers and secure assured products, especially where existing guidelines and regulations do not require other parties’ compliance.
Understanding NCSC Principles and Recommendations
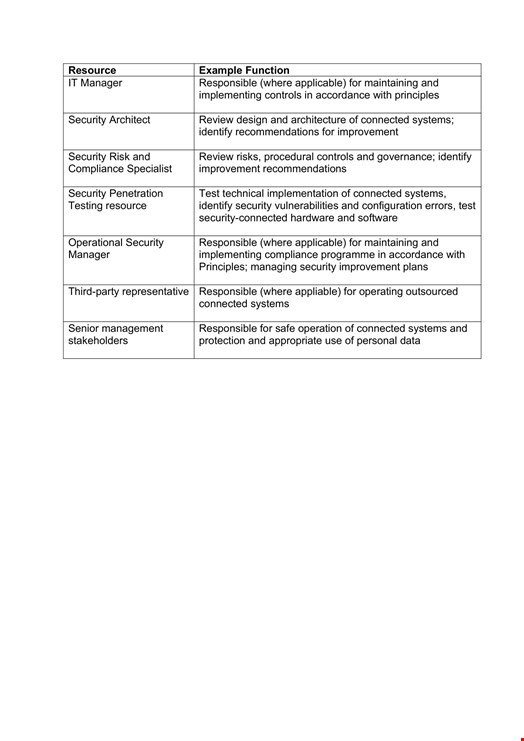
Core aspects of the principles are split into three, providing a blueprint for authorities to understand, design and manage their connected places.
This means understanding its potential impacts, risks, cybersecurity governance and skills, roles of suppliers and legal and regulatory requirements.
Designing your connected place involves designing systems, architecture and monitoring to reduce exposure, protect data and build resilience and scalability.
Managing your connected place needs to include managing privileges, incidents and supply chains and response and recovery plans.
Authorities will face challenges implementing the principles, but the concept is not new to authorities used to managing IT systems and large volumes of personal data.
A High-Level Road Map for Principle Implementation
This table outlines the tasks required to implement the principles in authorities.
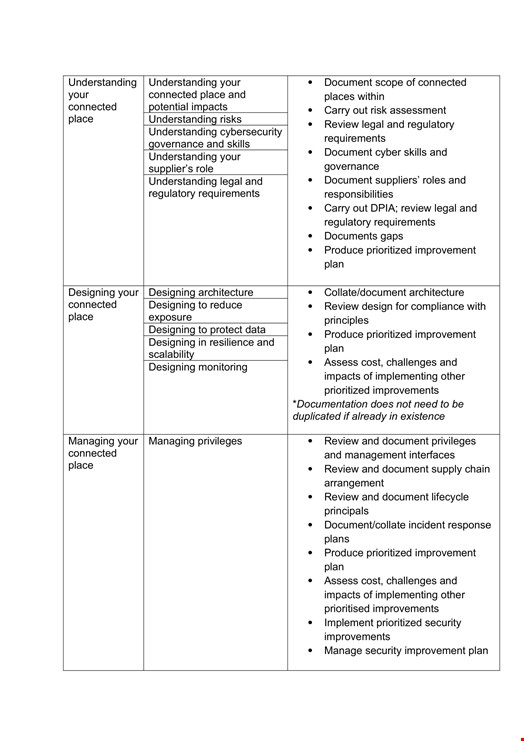
Resources
Resources are crucial to successful principle rollout. The table below provides an overview of key functions required to implement and manage compliance.