Nettitude’s senior research analyst, Dr Jules Pagna Disso, sets out eight considerations for organizations looking to deploy a cyber-threat intelligence solution
Protecting against cyber-attacks is proving to be a real challenge. A few years ago, defense-in-depth was the recommended methodology to successfully fight cyber-attacks. Despite the proliferation of defense-in-depth mechanisms, a large number of high profile cyber-attacks are still observed. According to a survey by Forrester’s Forrsights Security Survey in 2013, 75% of 490 companies agreed that cyber-threat intelligence was a priority. The recent 2015 Global Megatrends in Cybersecurity report suggested that most companies will deploy cyber-threat intelligence over the next three years as a measure against cyber-attacks.
Common Basic Errors Found in Cyber-Threat Intelligence
Cyber-threat intelligence (CTI) can be categorized into the tactical intelligence that will help CISOs, CIOs and CEOs support the security strategies of their environment, and operational intelligence that can be used by analysts to manage attacks on a daily basis. Having used a good number of the so-called CTI solutions, I have observed that many companies do not understand what they are paying for. Here are eight key areas worth considering before deploying a CTI solution.
1: A large number of internet protocol addresses (IPs) will not provide cyber-threat intelligence
A large number of IPs is not a guarantee that a cyber-attack is going to be prevented.
2: A large number of alerts
It is not a surprise for those who work as intrusion analysts to know that most analysts deliberately turn off certain distribution lists or rulesets because they are too ‘noisy’. It makes little sense that analysts react to less than 1% of alerts. When rulesets are turned off, it is very likely that an attack will go undetected. As strange as it may sound, a good CTI solution should reduce the number of alerts.
3: Fancy dashboards – all that glitters is not gold
Having a fancy dashboard does not necessarily help in understanding how to protect against cyber-attacks. Dashboards need to speed up the process of decision-making, hence providing enough intelligence to trigger a reaction either from the management or from the operators.
4: All data has the same value
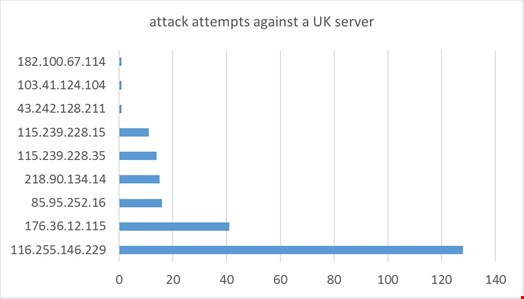
Figure 1 shows a list of IP addresses abusing a server. It appears that the attacker behind IP 116.255.146.229 has much more time on their hands than for the IP 182.100.67.114. The number of attempts is not the only criterion that can be used to determine the seriousness of the attacker. There are certainly many factors involved for a cyber-attack to be successful, such as motivation and the value of the information. This simple illustration, however, shows that the different IPs could present different threat levels.
5: No or poor contextual information
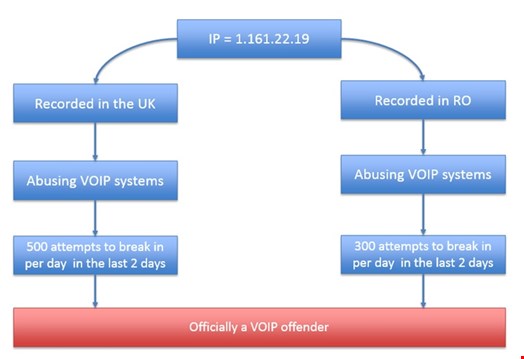
Figure 2 evidences that contextual information is very important. IP 1.161.22.19 was recorded attacking different servers across the world that were targeting the same service. The level of controls put in place to stop cyber-attacks should leverage a protection proportional to the threat level. An organized crime group targeting your environment would inevitably present a different threat level than a single attacker.
6: Threat intelligence that solves all cyber-attack problems – ease of configuration
Threat intelligence should be specific to a threat. The lack of targeted intelligence is in part due to the fact that CTI is, in most cases, gathered randomly around the globe, with no specific objective. CTI solutions should be able to provide threat analysis specific to one organization.
7: Bad forever – no revalidation of threat intelligence
A recent study has found that the union of 15 public blacklists includes less than 20% of the malicious domains for a majority of prevalent malware families. There is a popular view that cyber-threat intelligence generates a large amount of data to be analyzed. This is not necessarily true when it comes to cyber-threat intelligence, as there is a big risk that enterprises will be overloaded with data that has lost its value.
8: No risk assessment
Cyber-threat intelligence certainly has its value in helping to protect against cyber-attacks. However, CTI should not be confused with a mere collection of cyber-attack related information. A CTI deployment without risk analysis would be of very little help. Defense-in-depth strategies need to incorporate information taken from threat intelligence. Effective threat intelligence should be based on facts and should be actionable tactically or operationally.
Protecting against cyber-attacks is not a simple task. Spending a lot of money will not necessarily solve the problem. It is fundamental to know what we are protecting, why we are protecting it, and more importantly, who we are protecting our assets from.
About the Author
Dr Jules Pagna Disso has over 15 years’ experience working in cybersecurity. Currently leading research into malware and threat intelligence at Nettitude, Jules was previously the head of EADS’ cybersecurity research lab in the UK, where he was the technical lead for all cybersecurity related projects. He also provides consultancy services for various organizations on critical infrastructure security and holds a PhD in Intrusion Detection Systems as well as a number of cybersecurity related qualifications.
