Despite global ransomware cyber-attacks having plunged businesses all over the world into chaos, many organizations remain out of their depth when it comes to properly protecting themselves against these growing threats.
With a range of services - including Skype, Office and OneDrive - available within Microsoft’s Office 365 platform, Microsoft’s productivity suite provides users with the unique benefit of accessing these applications when and where they need it.
As we fast progress towards becoming a digitally-first nation, this is especially significant for organizations who are moving to introduce flexible working policies to allow their employees to maintain a work-life balance as well as improve productivity and efficiency within the business.
However, as with any applications used or operated over an online platform, O365 can open up a number of potential threats to its users. Most recently, our Cyber Threat Intelligence research identified a new threat emanating from West African threat actors who are successfully compromising legitimate credentials via Microsoft O365 chain phishing.
What is a chain 365?
Compromising organizations since around June this year, the attack starts with an organization receiving a phishing email from an organization in their supply chain with a landing page requesting the input of Office 365 credentials. Once the credentials are compromised, the attacker uses these to phish further internal and external contacts via a different landing page.
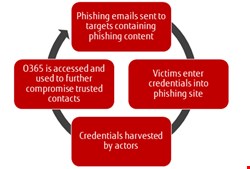
Although phishing is not a new concept, the risk can be amplified to O365 customers. Using legitimate credentials can allow access to other Microsoft services within an O365 environment such as Skype, SharePoint and OneDrive.
A successful phishing lure, targeting an O365 user, will start a series of events via a chain methodology. However, the most important thing to remember is that the threat actor can choose who to target and how to target them. For example, the threat has been seen to extend to business email compromise, posing a significant risk of financial loss to an organization.
Given the potential for access to key data stored in O365, an attack such as this represents elements of corporate identity theft, creating the ability to interact with both internal and external users posing as a trusted individual and the onward chain of infection. It highlights the serious potential for damage this attack can cause.
So why should organizations tread carefully? This attack is often successful due to mail being sent by what appears to be a legitimate individual. If someone has had contact with an individual they are far more likely to trust and interact with content they provide. Given the ability in this attack scenario to further communicate via Skype, this could easily sway even tech savvy users to let their guard down.

Best practices for safeguarding your organization against an attack
There are measures that an organization can take to reduce the chances of becoming victim to this sort of attack. For example, the configuration options Microsoft allows offer numerous remediation steps and more complex configurations which guard against potential compromise. These options include, but are not limited to: data loss prevention, multi-factor authentication and advanced threat solutions.
Whilst these options reduce risk, they don’t necessarily remove it altogether. It’s important that companies communicate these potential threats with employees by providing guidance on how to look out for changes in behavior. For example, if there is an email from a colleague which looks a little strange, make sure they are well versed on the steps that should be taken to escalate these concerns to the relevant IT departments.
As businesses continue to move more of their operations online, there will always be the security elephant in the room. However, if simple measures are put in place, businesses can ensure they’re running less of a risk of compromising important or sensitive information.
