"It appears the profile is being actively used to view the profiles of intended targets", reported Websense Security Labs in a blog posting Thursday. "Any LinkedIn user can see the most recent 5 users who have viewed their profile, and most users are keen to understand who may have done so."
A scammer can use LinkedIn's search features to locate potential targets. A premium account holder, as is this account, can include advanced search elements such as job function, seniority level, and company size. LinkedIn has more than 250 million members, and includes executives from all of the 2013 Fortune 500 companies.
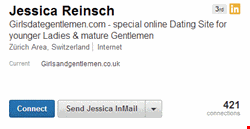
Having located potential targets, the scammer need only visit those target accounts to encourage interest. And it would appear to be successful. Seeing a visit from a smiling young blond lady, demurely not provacatively dressed, most men would visit-back to learn more. The Jessica Reinsch account, still active at the time of writing, boasts 421 contacts. More surprisingly, if Websense is correct, it includes dozens of endorsements (all from men) that reads like a minor who's who of businessmen. The endorsed subjects range from social media marketing to legal writing and commercial litigation.
Jessica Reinsch's website, however, is given as girlsandgentlemen dot co dot uk – a dating site geographically hosted in Switzerland. "In this case we believe that the dating site is used merely as a lure," writes Websense.
"At the time of writing no malicious code exists on this dating website, but we do have telemetry revealing that other domains on that same IP have been known to host suspicious code such as blackhat SEO," warns the company. "We also see that IPs used to host the dating site are hosted within the same Autonomous System Number (ASN) as multiple Exploit Kit Command and Control URLs, including RedKit and Neutrino exploit kits."
Furthermore, by enticing potential targets to connect on LinkedIn, an attacker is in a strong position to glean the personal information that will make a future spear-phishing attack – particularly when the phish comes from a recognized contact – all the more likely to succeed.
"As business profiles are big currency to cybercriminals," comments Carl Leonard, senior security research manager EMEA at Websense, "it’s unsurprising that LinkedIn profiles are now being used to lure users to click on links that could lead to the darker places of the web."